Install an Active Directory read-only domain controller (RODC) on Windows Server 2016
- Windows Server
- 14 May 2021 at 18:47 UTC
-

- 2/2
4. Change the delegated administrator of a read-only domain controller (RODC)
At the "RODC options" step of the wizard, you had the option of defining a delegated administrator for this domain controller.
If you want to change or add it, open the properties of the computer object corresponding to your read-only domain controller (RODC).
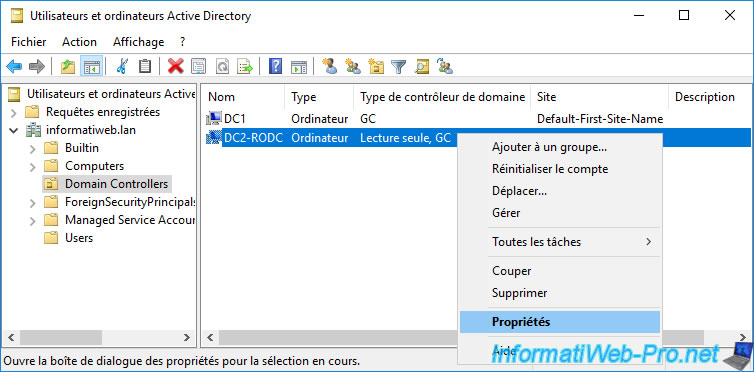
In the "Managed By" tab, you will see the information "The selected group can administer this RODC".
Click on : Change.
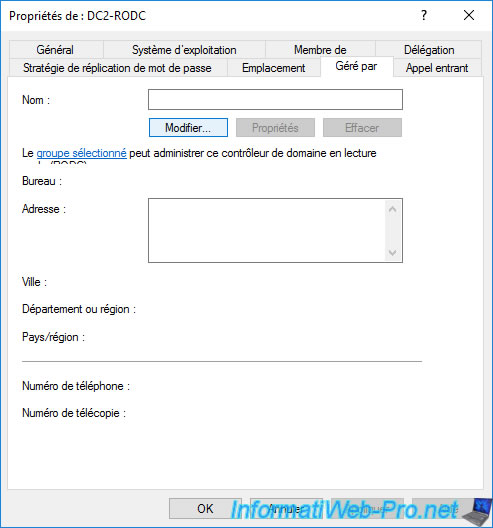
Specify the name of an Active Directory account that you want to allow to manage your read-only domain controller (RODC).
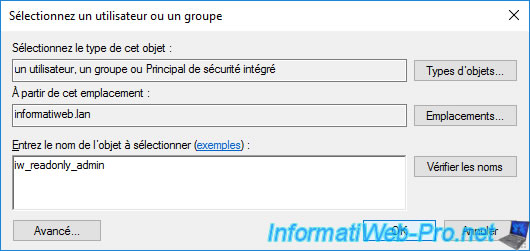
The selected account appears.
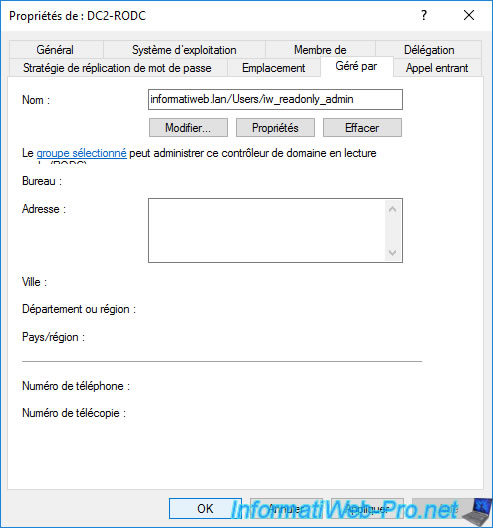
Although this is not mandatory, it may be interesting to add the account chosen as delegated administrator to the "Allowed RODC Password Replication Group" group.
This allows to authorize the read-only replication of the password of this account on the read-only domain controller (RODC) concerned and thus allow this account to be able to manage this domain controller even if the network link between the RODC and other domain controllers is not currently available.
In short, open the properties of the account you have chosen previously, go to the "Member of" tab and click "Add".
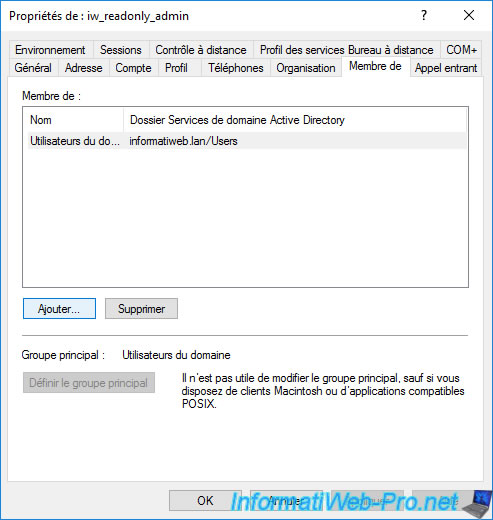
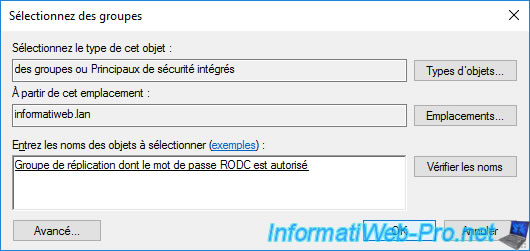
Find the "Allowed RODC Password Replication Group" group by using the "Advanced" button, then click OK.
Note that the delegated administrator of the read-only domain controller (RODC) can only edit users who are in the "Allowed RODC Password Replication Group" group.
However, he will not be able to modify other objects and user accounts.
Indeed, as you can see, everything is grayed out.
5. Password replication policies
Open the properties of your Active Directory read-only domain controller (RODC).
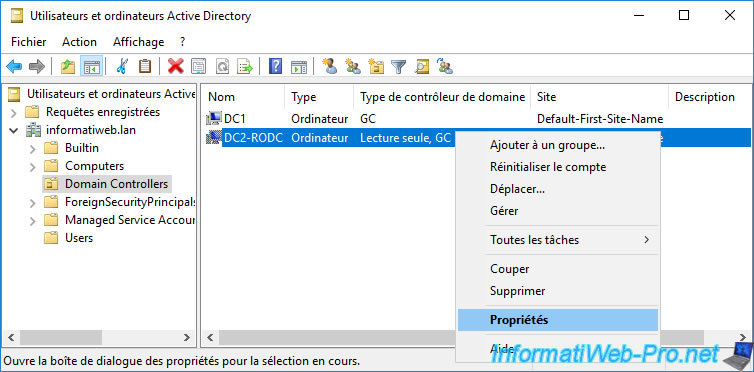
Since this is a read-only domain controller (RODC), a "Password Replication Policy" tab is present in its properties.
To allow or deny password replication for a new user, a new group or a new computer, click "Add".
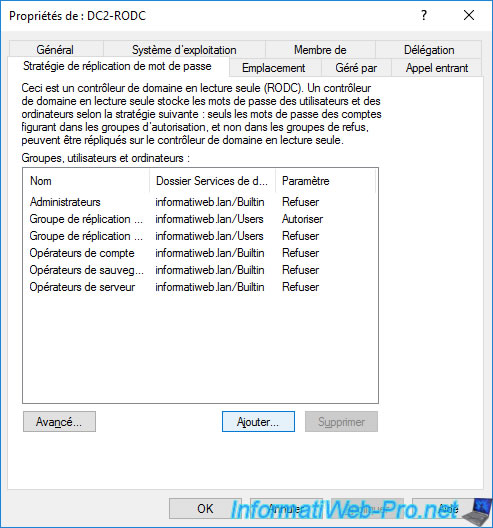
Choose whether you want to allow or deny password replication on this read-only domain controller (RODC) and click OK.
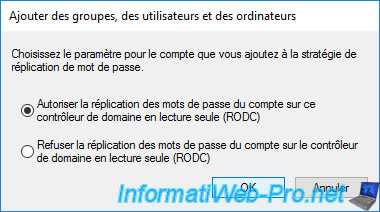
Then, specify the name of the user, group or computer you want and click OK to add it to the list.
If you click on the "Advanced" button present in the "Password Replication Policy" tab, an "Advanced Password Replication Policy for [RODC server name]" window will appear.
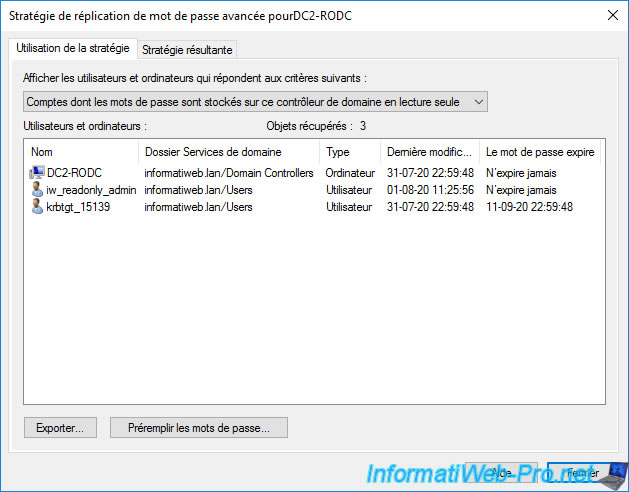
By default, the choice selected is : Accounts whose passwords are stored on this Read-only Domain Controller.
Which means that this is the list of users for which the password is stored on this read-only domain controller.
When these users attempt to connect to a client workstation, the connection request can therefore be processed directly by this read-only domain controller (RODC).
Note that the "krbtgt_*****" account is a KRBTGT account used by read-only domain controllers (RODC) and that this account has a different password than writable domain controllers.
Source : Read-only domain controllers and the KRBTGT account
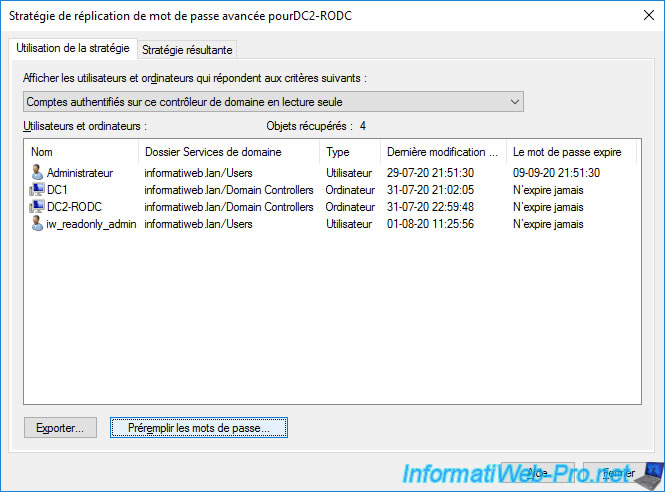
If you choose "Accounts that have been authenticated to this Read-only Domain Controller", this will be the list of users who have already authenticated on this read-only domain controller (RODC).
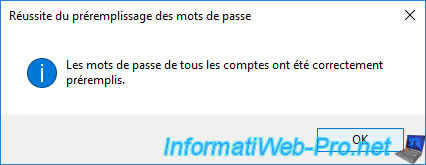
To speed up authentication of users whose passwords can be replicated on this read-only domain controller, you can prepopulate the passwords for them by clicking : Prepopulate Passwords.
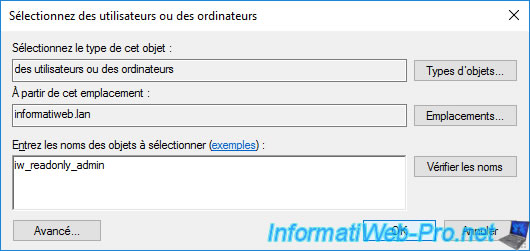
Provide the name(s) of the user(s) whose passwords you now want to replicate on this read-only domain controller (RODC) and click OK.
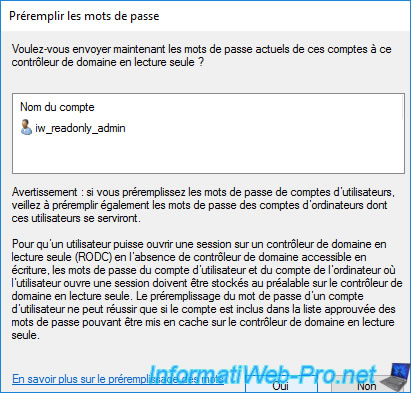
Confirm the password filling on this domain controller and click Yes.
Click OK.
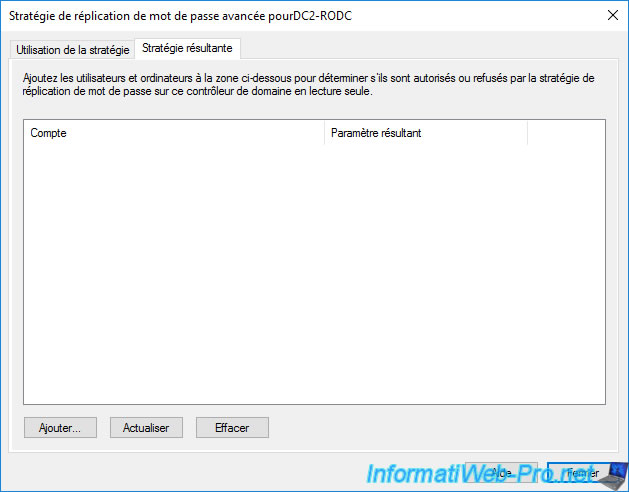
If you want to check if the password is allowed to be replicated or not, go to the "Resultant Policy" tab.
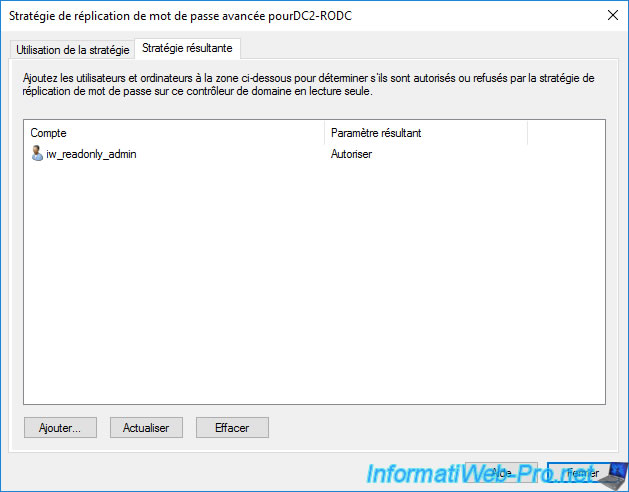
Click "Add", enter the name of a user, then click OK.
The resultant setting will indicate whether password replication is allowed or denied for this user.
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain

No comment