- Windows Server
- 11 June 2021 at 18:26 UTC
-

In an Active Directory infrastructure, you can create external trust relationships (domain trusts), as well as forest trust relationships.
However, before creating trust relationships, it's essential to understand how they work and what they entail.
For this, refer to our article : The basics of Active Directory Domain Services (AD DS)
In this tutorial, we will create an external trust relationship between 2 domains present in 2 different forests.
In our case, we are going to create an external trust relationship between our "web.informatiweb.lan" and "corp.informatiweb-pro.lan" Active Directory domains.
To create an external trust relationship between 2 domains, open the "Active Directory Domains and Trusts" console and right-click "Properties" on the source domain (in our case : web.informatiweb.lan).
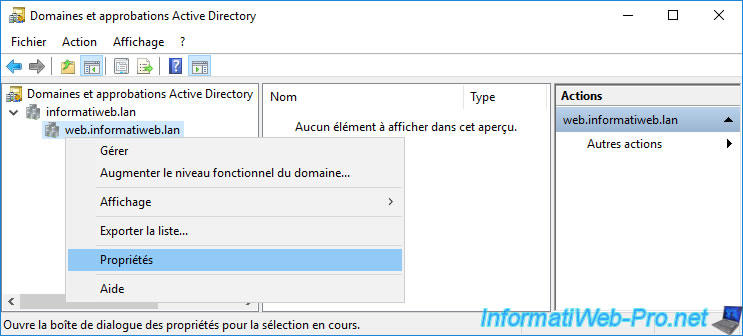
Then, go to the "Trusts" tab and click on the "New Trust" button.
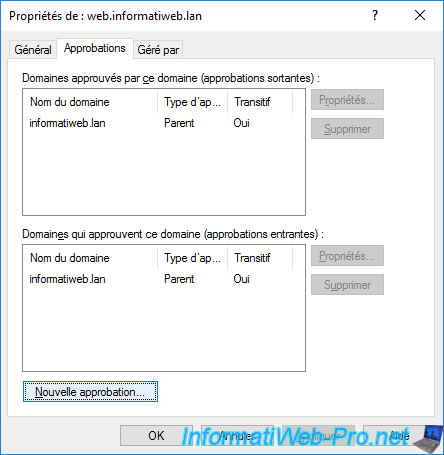
The New Trust Wizard appears.
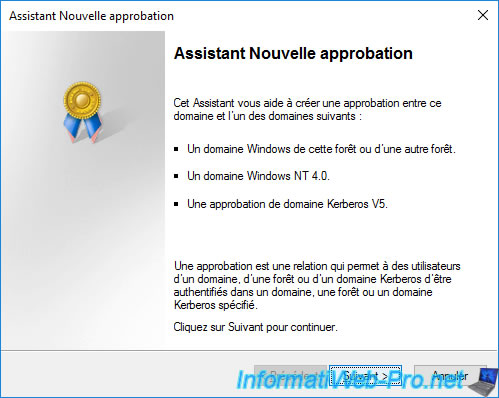
Specify the destination domain name with which you want to create the external trust relationship (domain trust).
In our case : corp.informatiweb-pro.lan
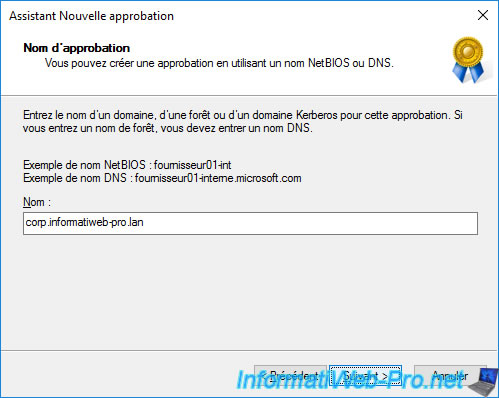
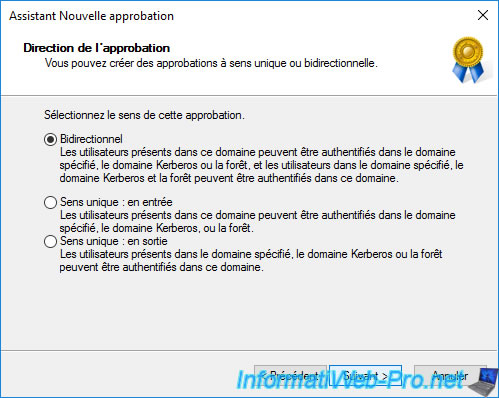
Choose the direction of this trust :
- Two-way : users from the source domain can be authenticated in the destination domain (and vice versa)
- One-way - incoming : users of the source domain (in our case : web.informatiweb.lan) can be authenticated in the destination domain (in our case : corp.informatiweb-pro.lan)
- One-way - outgoing : users of the destination domain (in our case : corp.informatiweb-pro.lan) can be authenticated in the source domain (in our case : web.informatiweb.lan)
For a trust relationship to be valid, the trust object you are creating must be present on both sides (so in the source domain and the destination domain).
The wizard therefore asks you if you want to create this trust in :
- This domain only : the source domain. In our case: web.informatiweb.lan
- Both this domain and the specified domain : the source domain (web.informatiweb.lan) and the destination domain (corp.informatiweb-pro.lan)
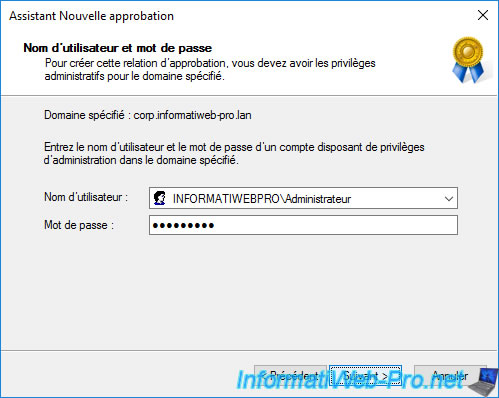
If you know the credentials of an account authorized to create trust relationships in the specified domain (destination domain : corp.informatiweb-pro.lan), then select "Both this domain and the specified domain".

As we have chosen to create the trust in the source domain AND in the specified domain (destination domain), the wizard asks us for the credentials of an account with administrative privileges in the specified domain.
When you create a trust relationship, the wizard offers you to choose between :
- Domain-wide authentication : allow access to all resources of the local domain (source domain) from the specified domain (destination domain)
- Selective authentication : limit access to resources in your local domain (source domain)

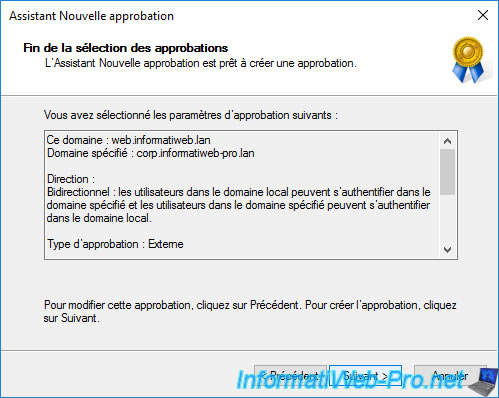
A summary of the trust relationship configuration appears before it's created.
Since the local domain name and the specified domain are not root domains, the wizard will automatically detect that this was an external type trust relationship (as shown in the summary displayed).
To create this trust relationship, click "Next".
Now, the trust relationship has been created.
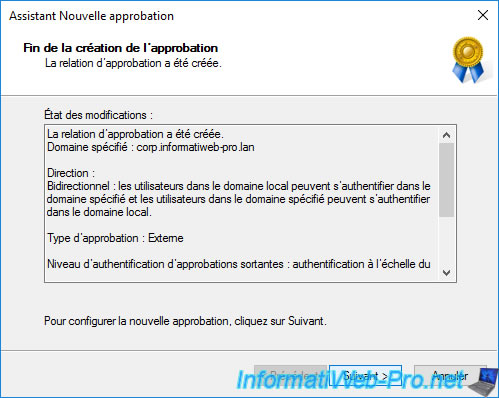
In order for this trust relationship to be used, the incoming and/or outgoing trust (depending on the choice made at the start of the wizard) must be confirmed.
As we have created a two-way trust relationship, we need to confirm the outgoing trust and then the incoming trust.
Select : Yes, confirm the outgoing trust.
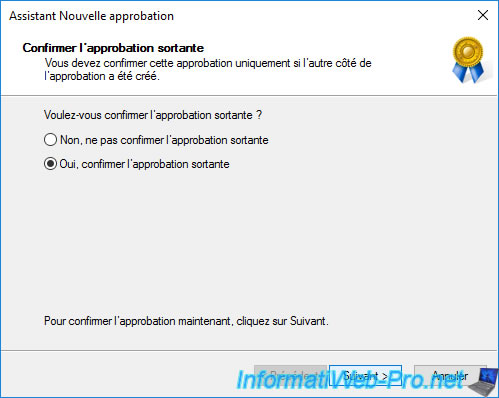
Then : Yes, confirm the incoming trust.
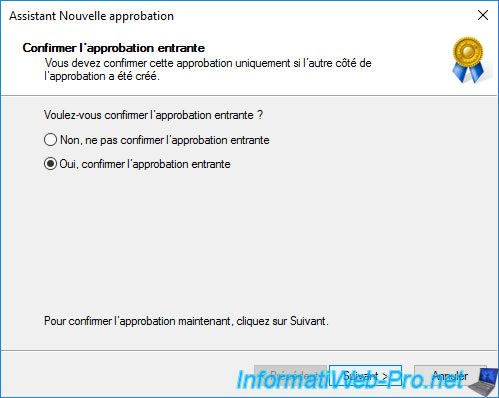
Your trust relationship has been created and confirmed.
Click on Finish.
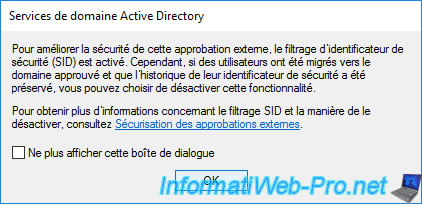
When you create an external trust relationship, SID (Security Identifier) filtering is automatically enabled as a security measure.
SID filtering prevents malicious users with administrator rights to the domain or forest from granting themselves elevated rights in the remote forest through the trust relationship created.
It also avoids attacks that use the history of SIDs which is used at the base to simplify the migration of many users without having to update the rights on the various resources of a server.
To learn more about this SID filtering, refer to these official Microsoft pages :
- Configuring SID Filtering Settings
- SID Filtering
In the "Trusts" tab of the properties of the source domain (in our case : web.informatiweb.lan), you will find 2 new "External" and not-transitive type trust relationships.
This means that the relationship is only valid between the 2 domains concerned and that we cannot go further than these 2 domains using this trust relationship.
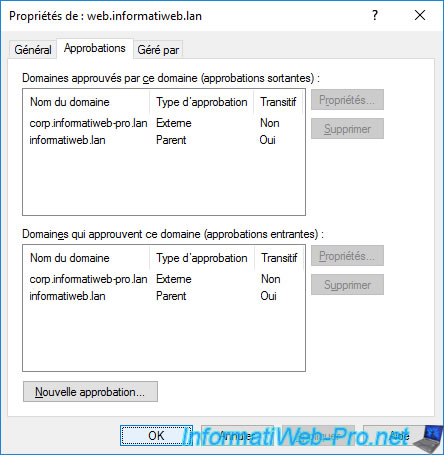
If you view the properties of the trust relationships you just created, you will find :
- the local domain (source) : web.informatiweb.lan
- the domain specified previously (destination) : corp.informatiweb-pro.lan
- the trust type : External = domains trust
- a box indicating whether the domain supports Kerberos AES encryption
- the direction of trust : Two-way
- whether the trust is transitive or not
- a button to validate this trust relationship (if it has not already been validated)
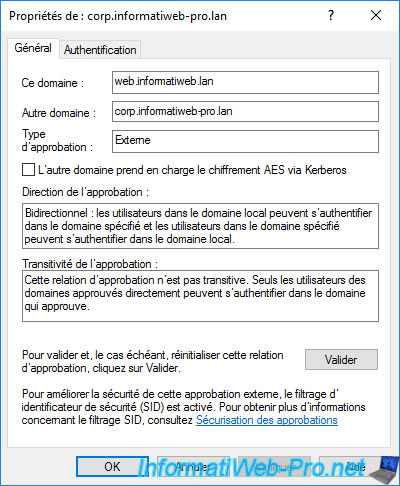
In the "Authentication" tab, you can choose whether you want to limit or not the access to resources in the local domain (web.informatiweb.lan).

Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain

You must be logged in to post a comment