Configure a multi-site Active Directory infrastructure on Windows Server 2022 and 2016
- Windows Server
- 10 November 2025 at 17:31 UTC
-

- 5/11
11. Configure Active Directory sites
Configuring Active Directory sites is critical, because at this time all of our domain controllers are in the same Active Directory site. Which means Active Directory currently believes that all of our domain controllers are physically in one place.
So that Active Directory can automatically adapt its replication topology and so that client PCs can connect to the domain controller closest to them (to speed up session openings, ...), you must configure the Active sites Directory and associate the different subnets used on each site.
Once the Active Directory sites and the subnets are configured and associated correctly, you can choose when you want to replicate the data between each site, define which network link is faster than another, ...
11.1. Create Active Directory sites
To start, open the "Active Directory Sites and Services" console and right-click "New Site" on the "Sites" folder.

Create the "Brussels" Active Directory site which corresponds to the physical site of the same name.
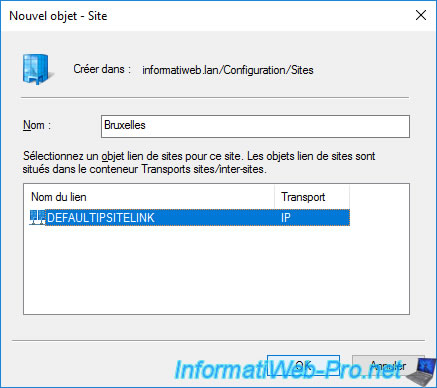
When creating the 1st Active Directory site, the "Active Directory Sites and Services" console displays a message telling you that you must :
- ensure that this site is linked with the correct site links. This defines the physical network link that connects this site with this or that other physical site.
- add subnets used on this physical site and associate them with this Active Directory site
- install domain controllers at this site and move them to this site. In our case, the domain controllers have already been installed, so it will be enough to move them to the correct Active Directory site.
Create a "Paris" Active Directory site for that of Paris.
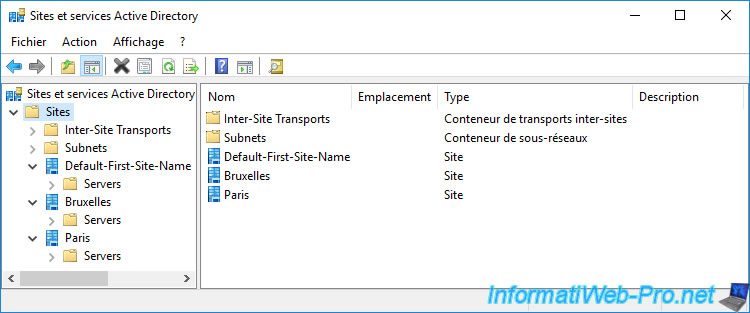
For the moment, we therefore have 3 Active Directory sites :
- the "Default-First-Site-Name" Active Directory site created by default which currently contains all our domain controllers
- the Active Directory site associated with the physical Brussels site, but which is empty for the moment
- the Active Directory site associated with the physical Paris site, but which is also empty
11.2. Define the subnets used on the different Active Directory sites
In order for client PCs to know which domain controller is closest to them, Active Directory will be based on the subnets defined here.
Defining these subnets also automatically associates new domain controllers with the correct Active Directory site.
Right click "New Subnet" on the "Subnets" folder.

In our case, the subnet used at Brussels is : 10.0.1.0/24.
So, we specify this subnet in the "Prefix" box and we select the "Brussels" site to specify to Active Directory that this subnet is located at the Brussels site.
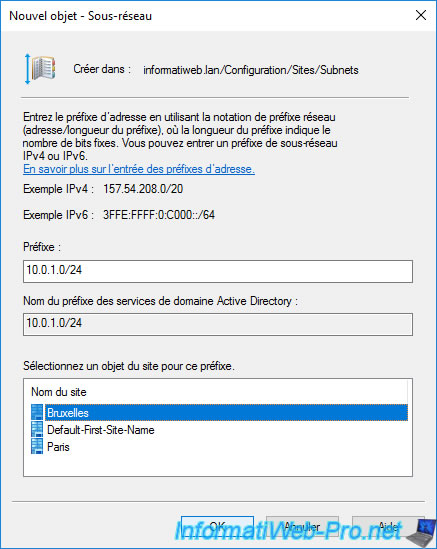
For the Paris site, the subnet is : 10.0.2.0/24.
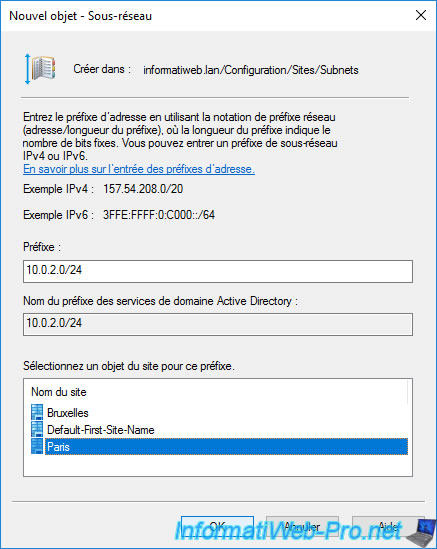
Active Directory now knows that :
- the "10.0.1.0/24" subnet is located in Brussels
- the "10.0.2.0/24" subnet is located in Paris
Note that you can very well have multiple subnets in a single Active Directory site.

You can also find the list of subnets associated with an Active Directory site by viewing the properties of an Active Directory site.

In the properties of our "Brussels" Active Directory site, we find our "10.0.1.0/24" subnet.

And in the properties of our "Paris" Active Directory site, we find our "10.0.2.0/24" subnet.

11.3. Define site links
When you created your Active Directory sites, you must have selected the "DEFAULTIPSITELINK" site link since it's the default site link.
Since we only have 2 Active Directory sites, creating a new site link is not necessary since there is only one physical link connecting our 2 remote physical sites.
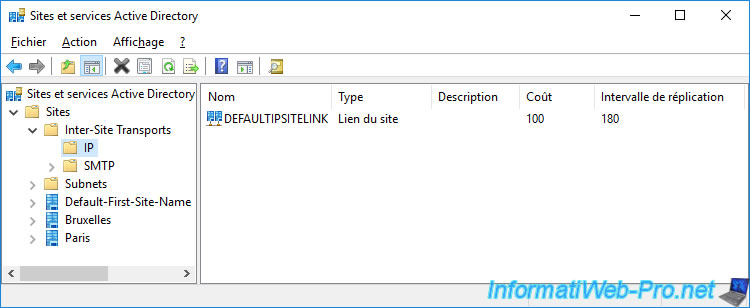
However, for the tutorial, we'll show you how to create a new site link.
To do this, right-click on the "Inter-Site Transports -> IP" folder and click on : New Site Link.

In our case, we are going to define the link which connects the site of Brussels with that of Paris.
So, we select the "Brussels" and "Paris" sites on the left and we click on the "Add" button, then click on OK.

The new site link appears.

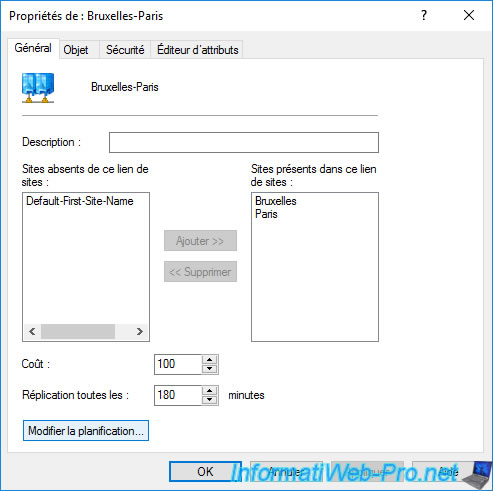
If you right click "Properties" on the site link you just created, you will see that you can :
- add a description for this link, if you wish
- change the Active Directory sites affected by this site link
- specify a cost for this site link. The cost being a value relative to other site links which indicates whether that link is much faster or slower than other available site links.
For example : a site link with a cost of 10 is considered 10x faster than a site link that has a cost of 100. - define the interval in minutes between 2 inter-site replications (= between the sites concerned by this site link)
- change the replication schedule
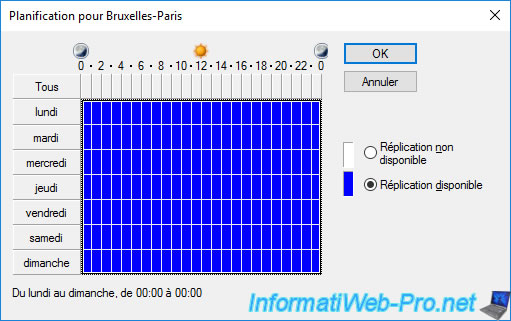
To change the inter-site replication schedule for this site link, click the "Change Schedule" button.
By default, replication is allowed every day of the week from 0:00 to 24:00.
But, for example, you can change this schedule so that inter-site replications only take place outside working hours and thus avoid slowing down your company's Internet access when your employees are working there.
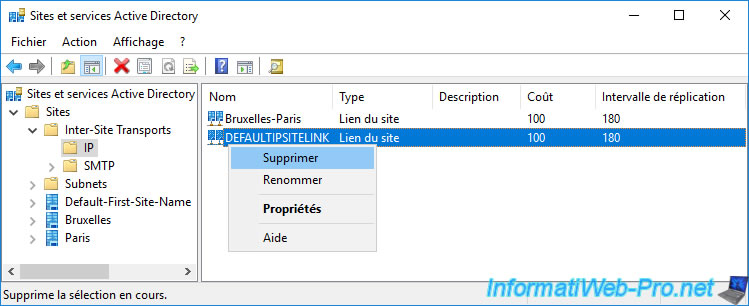
Since the default site link is no longer useful, it must be removed so that KCC can calculate the correct replication topology and not be influenced by this unnecessary link.
Right click "Remove" on the "DEFAULTIPSITELINK" site link.
And confirm the removal of this site link.
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain

No comment