- Windows Server
- 06 April 2019 at 11:18 UTC
-

- 1/2
When you publish desktops and/or RemoteApp programs, your users directly use published programs on your server.
This can be a problem if one of your users tries to play the smartest.
- Unauthorized Connection of a User in Remote Desktop Mode
- Secure your session host server with group policies (GPO)
1. Unauthorized Connection of a User in Remote Desktop Mode
Indeed, even if you only publish RemoteApp programs (which unpublishes the associated desktop), the user can very easily connect via Remote Desktop (thanks to the Windows RDP client) to access everything that is on your session host server.
The server address is not difficult to find since Windows displays the address when launching the 1st RemoteApp program and may even be identical to the one used to use the web access of the RDS solution.
For example, if our user launches the "Word 2013" program that we have published from our "RDS" session host server, he will know that the domain name of the session host server is : RDS.INFORMATIWEB.LAN
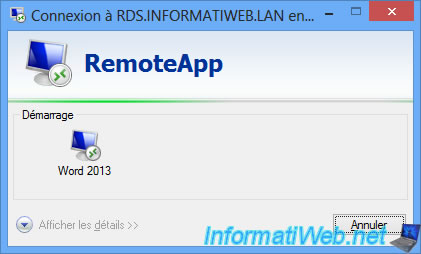
It is therefore enough for him to connect via the RDP client of Windows on this domain name.
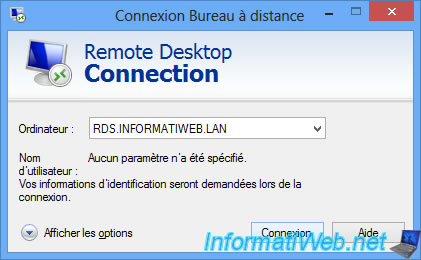
Enter its identifiers.
The session opens on the remote server.
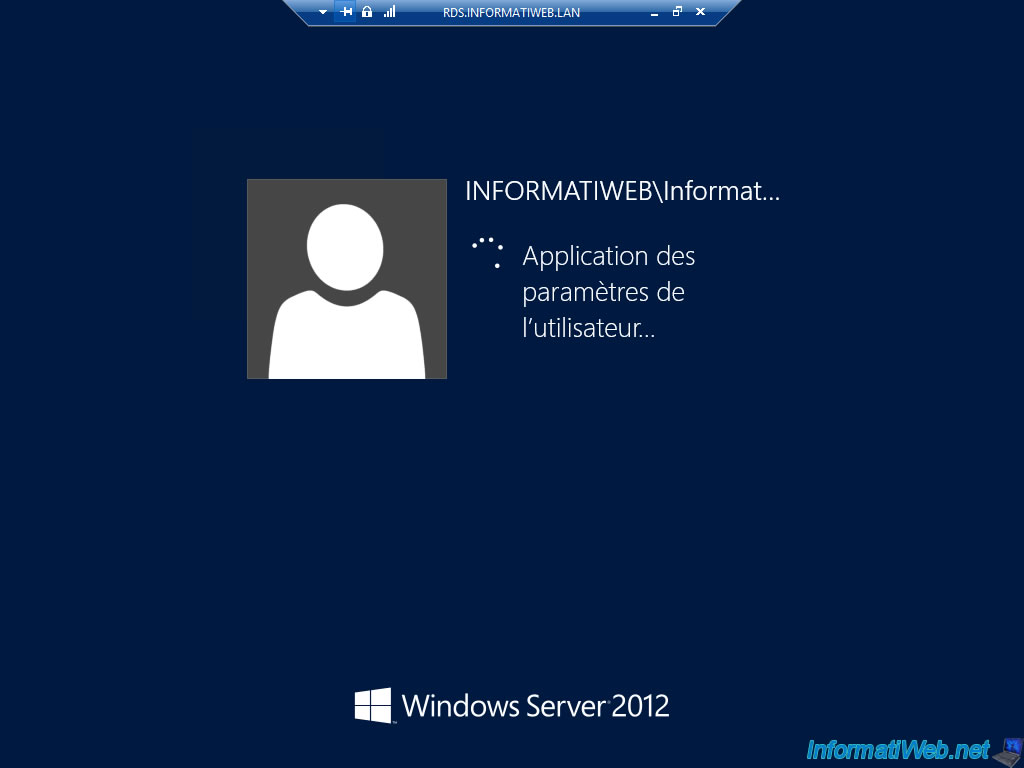
And your user arrives on a full session (limited by Windows basic permissions) and can therefore wander through the different options that are not restricted to administrators.
In short, this demonstration has the sole purpose of proving that this is easily possible and you should therefore consider securing a minimum your session host server to prevent a user makes you a bad joke.
In addition, you will not be able to block this access through Remote Desktop.
Indeed, you have allowed them to access this collection of desktops or RemoteApp programs.
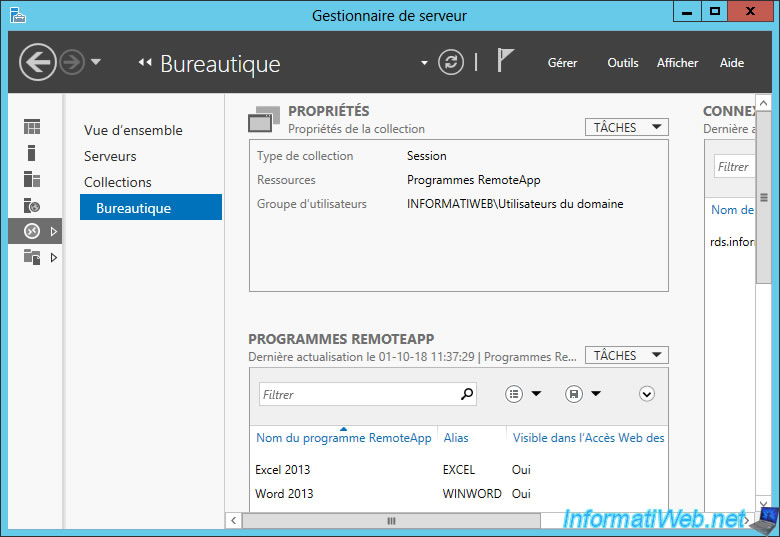
If you look in the computer management of your session host server, you will see that the same user group is a member of the local "Remote Desktop Users" group.
If your user is a member of this group, he can use the RemoteApp programs and the desktop through the RDP client. And if you remove it, it can't use any of the 2 features.
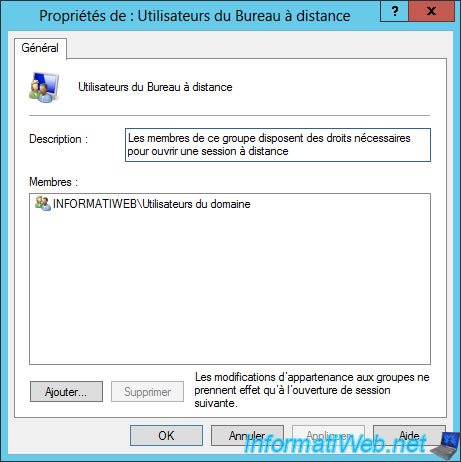
Moreover, as you can see in the description of this group, the members of this group have the necessary rights to log in remotely.
Share this tutorial
To see also
-

Windows Server 6/7/2019
WS 2012 / 2012 R2 - RDS - Set up HA on your RDS infrastructure
-

Windows Server 3/8/2019
WS 2012 / 2012 R2 / 2016 - RDS - Access RemoteApp via a modern application
-

Windows Server 4/28/2019
WS 2012 / 2012 R2 / 2016 - RDS - Attempt to unblock the session as a user
-

Windows Server 3/16/2019
WS 2012 / 2012 R2 / 2016 - RDS - Change the properties of RemoteApps


You must be logged in to post a comment