Restrict unauthorized remote desktop access to your RDS session host servers on Windows Server 2012 / 2012 R2 / 2016
- Windows Server
- 06 April 2019 at 11:18 UTC
-

- 2/2
2. Secure your session host server with group policies (GPO)
To begin, we will enable a strategy that will avoid bad jokes when you try to troubleshoot a server where the number of CALs would be insufficient.
In fact, for RDS users to be able to connect, there must be enough Client Access Licenses (CALs) on the license server of your RDS infrastructure.
If there are not enough, some users will be disconnected automatically when the following ones connect.
This may also happen to you if users attempt to reconnect because of an automatic logout (due to insufficient licenses).
To prevent you from being logged out because of a user, we recommend that you enable the "Deny log off of an administrator logged in to the console session" policy found in : Computer Configuration -> Policies -> Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Connections.
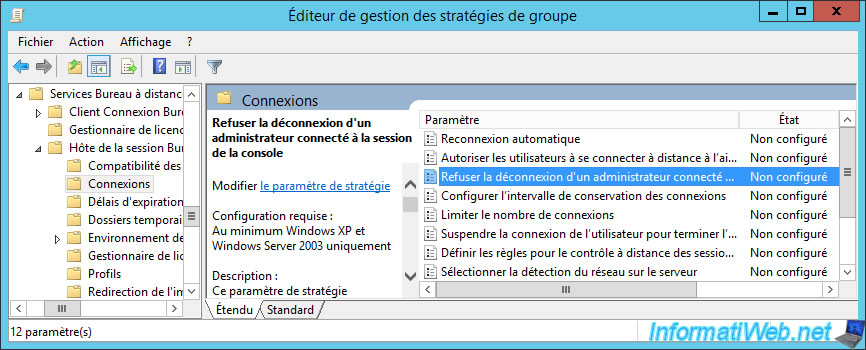
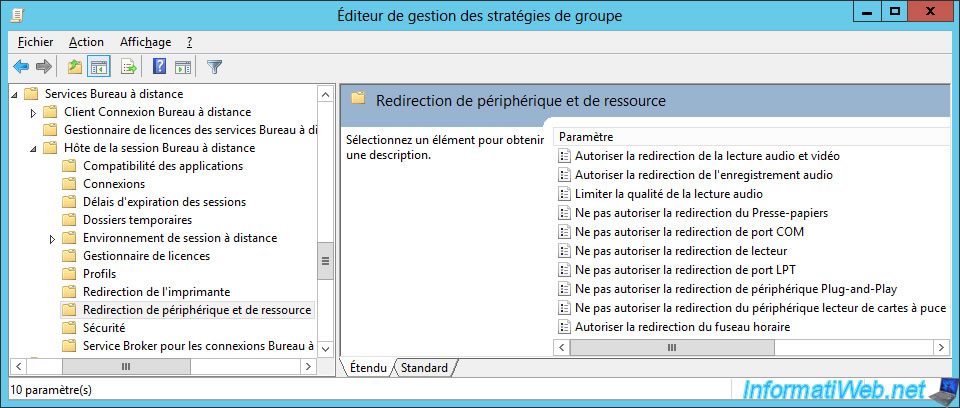
Then, to better secure your session host server and also avoid theft of data by a simple copy/paste, you can for example deny the redirection of :
- the clipboard : to block the copy/paste that everyone knows
- drives : to prevent your users from copying server data to one of their physical PC partitions and to avoid infecting your server with a virus on the client PC
- Plug-and-Play devices : to not redirect USB keys (which can be infected) and other Plug-and-Play devices
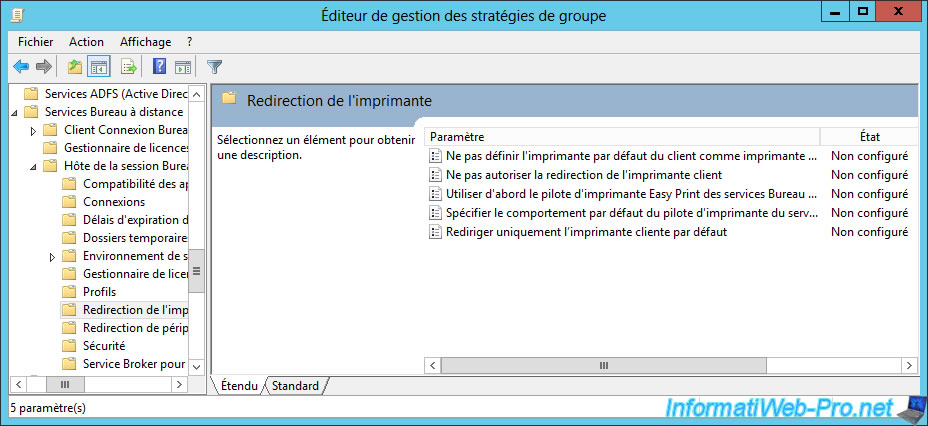
To avoid installing too many drivers and prevent your users from trying to install a malicious printer driver (which is complicated to create, but they exist), you can :
- disable client printer redirection by enabling this policy : Do not allow client printer redirection
- force your server to use the Easy Print driver for all redirected printers. This avoids the installation of additional printer drivers on your server.
- redirect only the default client printer : to limit the number of devices to redirect. Which is a good thing.
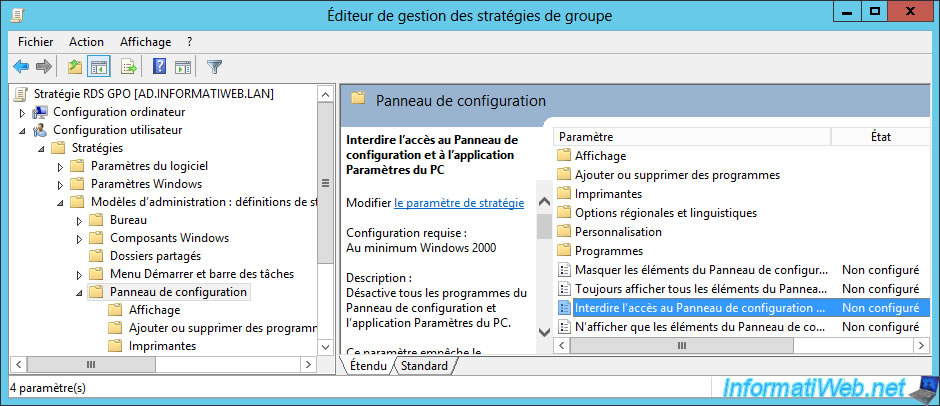
Now that you know that any user authorized to use a RemoteApp program can also easily connect to an entire Windows Server session, it makes sense to minimize the available interface on that server to prevent your user from walking around too easily on the server.
To get started, you can block access to the Control Panel by going to : User Configuration -> Policies -> Administrative Templates -> Control Panel.
In this folder, enable the "Prohibit access to Control Panel and PC Settings" policy.
Earlier, we told you about a strategy that allowed your server to first use the Easy Print driver for redirected printers from client PCs.
However, if the printer will not be supported by this driver, Windows Server may install the printer driver not supported by Easy Print.
To prevent this from happening and to avoid installing a malicious driver, you can enable the "Devices: Prevent users from installing printer drivers" policy available in : Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options.
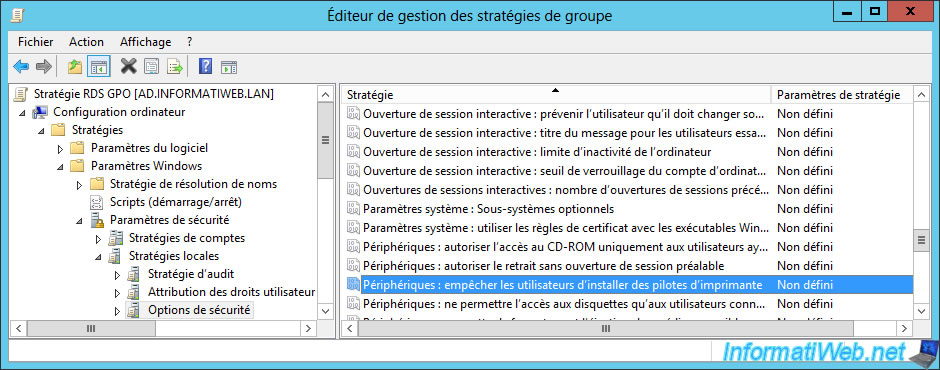
To prevent the user from hacking on your server, we recommend that you also block access to the registry, which is accessible via the "regedit.exe" program.
To do this, go to "User Configuration -> Policies -> Administrative Templates -> System" and enable the "Prevents access to registry editing tools" policy.
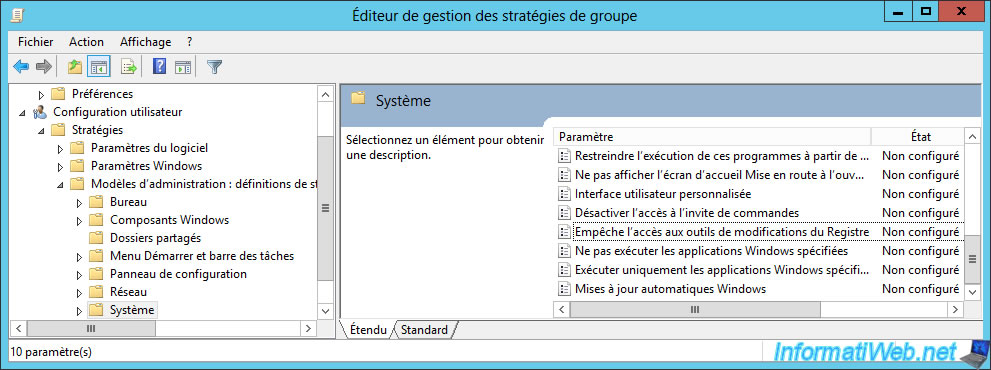
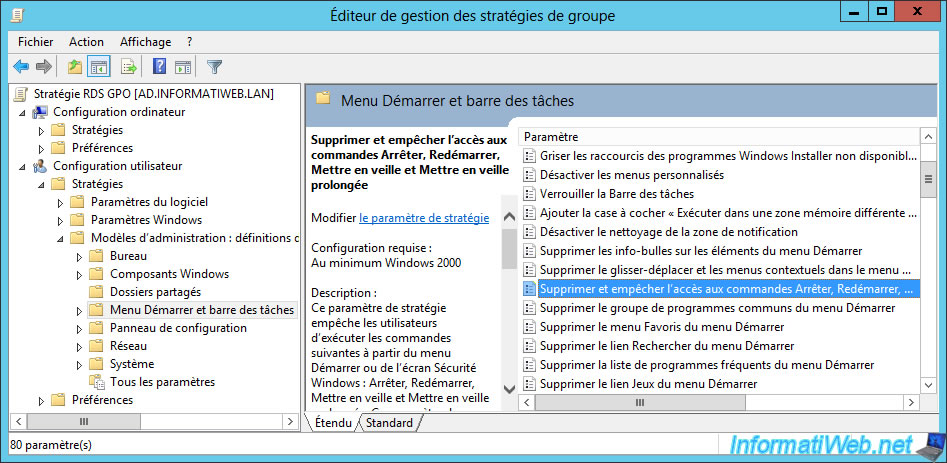
To limit the number of options displayed in the start menu (or the modern interface in Windows 8, 8.1 and higher), as well as in the taskbar, you can use the available policies in : User Configuration -> Policies -> Administrative Templates -> Start Menu and Taskbar.
Thanks to the many strategies available here, you can for example :
- clear the list of programs and documents that have recently been opened by your users
- lock the taskbar to prevent users from moving it
- remove and prevent users from shutting down, restarting, or hibernating the server
- delete the "Execute" option present in the start menu and which allows your users to launch any program (if avaible)
- hide the systray area : this will prevent your users from seeing which programs are running in the background on the server (including the anti-virus used, for example)
These policies are obviously to put in place if your users are supposed to use only RemoteApp programs and not the desktop directly.
In addition, the policies to apply will depend on your needs and/or the demand of your client (the company where you implemented the RDS solution).
In "User Configuration -> Policies -> Administrative Templates -> Desktop", you will also find some policies that may be interesting for emptying the desktop, or even making it unavailable.
For example, you can :
- hide everything on the desktop by enabling this policy : Hide and disable all items on the desktop
- remove only some icons of the desktop : workstation (or Computer), my documents, ...
![]()
Since all your users will only connect remotely (via the RDS solution) to your session hosts, you can safely enable these 2 group policies :
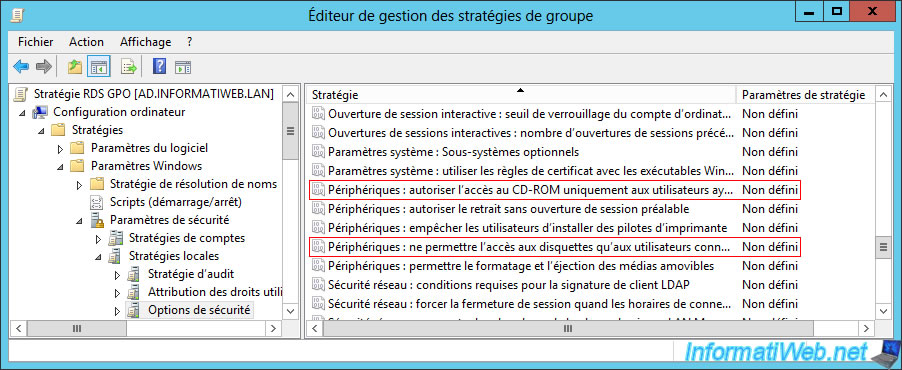
- Devices : Restrict CD-ROM access to locally logged-on user only
- Devices : Restrict floppy access to locally logged-on user only
This will prevent your users from playing remotely with the server's CD drive and floppy disk drive (if there are any).
Note : these policies can be found in : Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options.
To prevent users who like IT from launching anything on your server, it's interesting to block the access to the command prompt.
To do this, go to "User Configuration -> Policies -> Administrative Templates -> System" and enable the "Prevent access to the command prompt" policy.
Important : for this policy to be useful, don't forget to :
- enable the "Remove Run menu from Start Menu" policy located in : User Configuration -> Policies -> Administrative Templates -> Start Menu and Taskbar
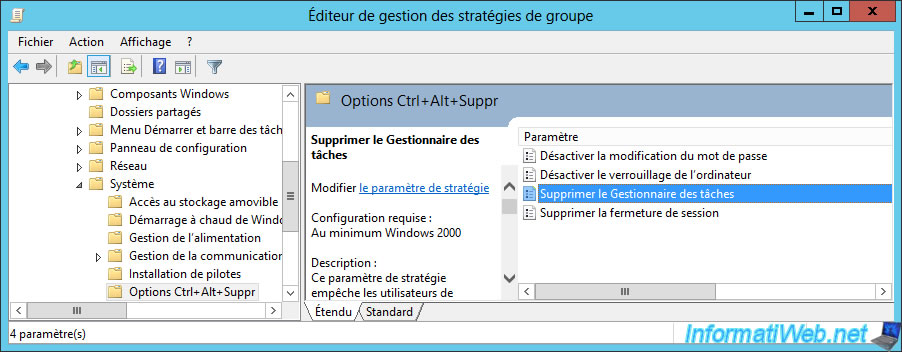
- block access to the task manager with the policy cited on the next image.
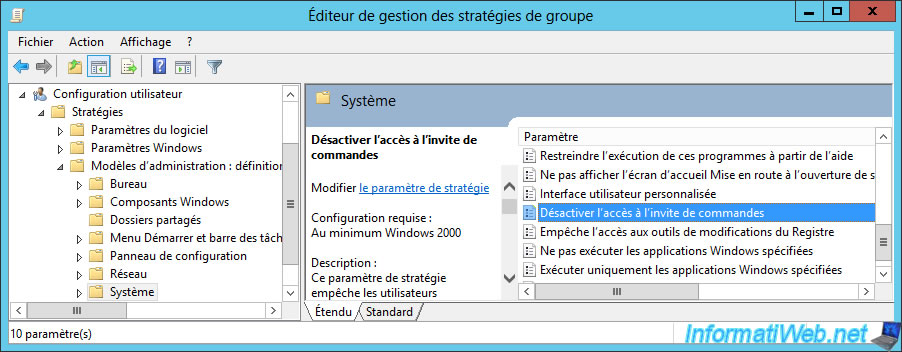
To block access to the task manager, go to : User Configuration -> Policies -> Administrative Templates -> System -> Ctrl+Alt+Del Options.
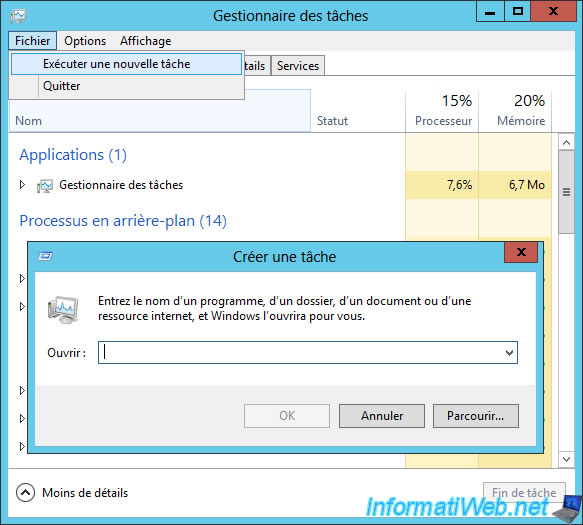
Then, enable the "Remove Task Manager" policy.
This will prevent the user from using the "Run new task" option that is an alternative to the "Run" option of the start menu.
Share this tutorial
To see also
-

Windows Server 6/7/2019
WS 2012 / 2012 R2 - RDS - Set up HA on your RDS infrastructure
-

Windows Server 3/8/2019
WS 2012 / 2012 R2 / 2016 - RDS - Access RemoteApp via a modern application
-

Windows Server 4/28/2019
WS 2012 / 2012 R2 / 2016 - RDS - Attempt to unblock the session as a user
-

Windows Server 3/16/2019
WS 2012 / 2012 R2 / 2016 - RDS - Change the properties of RemoteApps

No comment