Deploy the RDS gateway to provide secure access from the outside on Windows Server 2012 / 2012 R2 / 2016
- Windows Server
- 11 May 2019 at 17:29 UTC
-

- 3/3
7. Make your gateway accessible from the outside
Although your gateway allows you to connect to your network resources via remote desktop, the gateway is accessible via the HTTPS protocol (so on port 443).
To make your gateway accessible from the outside, you have 2 possibilities.
Place your RD gateway in DMZ in your router.
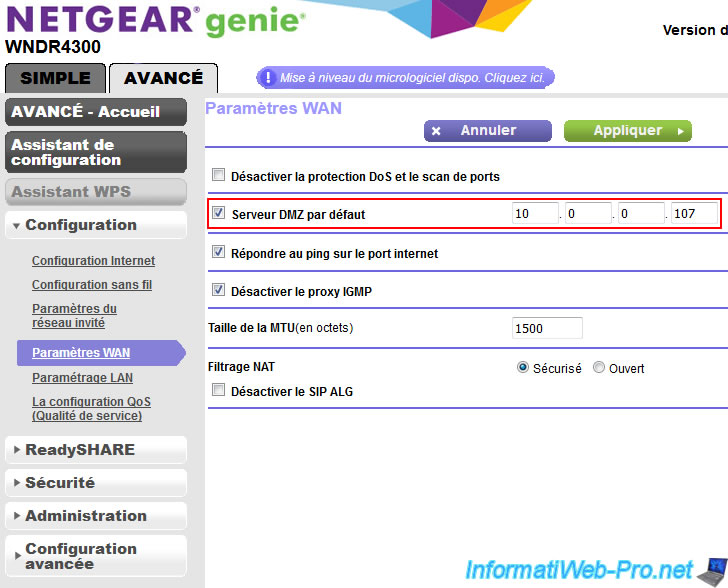
OR redirect port 443 (HTTPS) from your router to the server where you installed the RD Gateway.
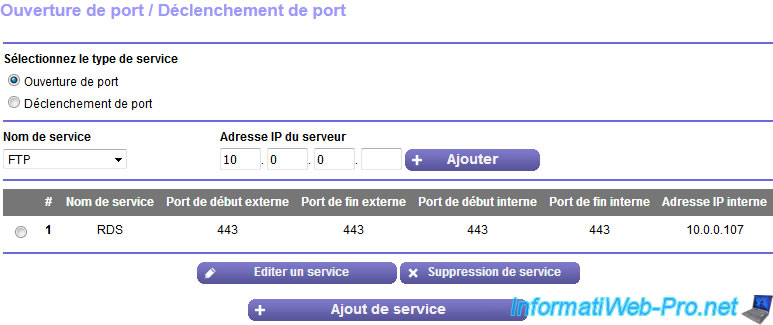
8. Test your RDS gateway
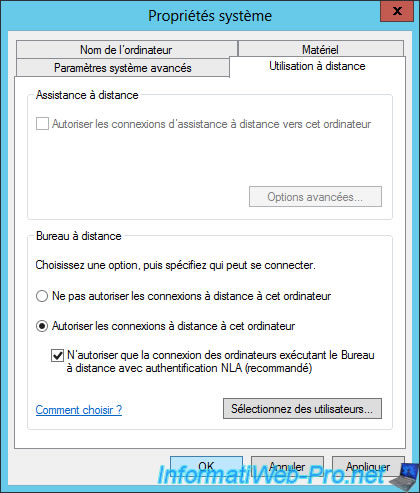
In order for your users to access a computer or server on the network, you must first enable Windows Remote Desktop on the destination PC.
For this tutorial, we will enable Remote Desktop on our Active Directory server.
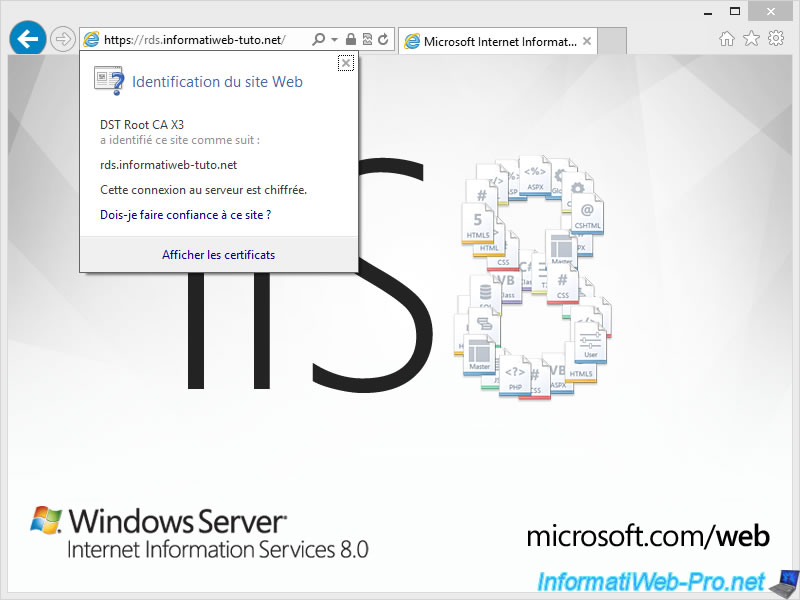
On a PC outside your network, try to access the address : https://[name of your server where the gateway is installed]
If your external domain and router are configured correctly, you will be able to see the default page of the Windows Server Internet Information Services (IIS) server.
As you can see, the connection is encrypted thanks to our SSL certificate.
Note that you will not be able to access the external domain name from within your network because loopback is often blocked by routers.
To overcome this problem, you can use our little trick.
To connect to a local server (in our case : our Active Directory server) from the outside, your users will first have to specify the local name of the computer they want to access.
Then, click on "Show Options".
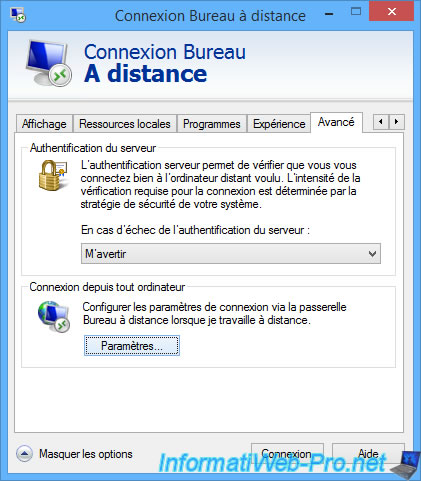
In the "Advanced" tab, click the "Settings" button in the "Connect from anywhere" section.
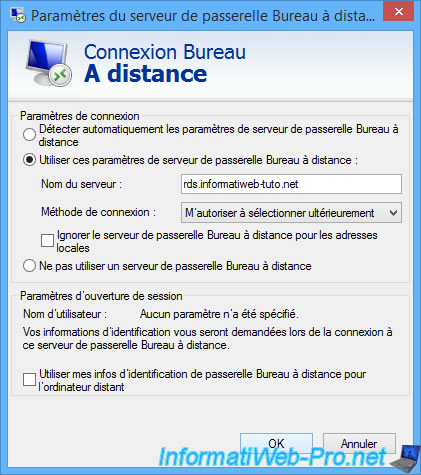
Select the "Use these RD Gateway server settings" option and specify the external domain name to connect to your RDS gateway.
Note : clear the "Ignore RD Gateway server for local addresses" check box.
To finish, click on : Connection.
Since the RDP connection will be through the Remote Desktop Gateway, Windows will ask you twice to login.
To begin, Windows will ask you for the credentials to use to connect to the RDS gateway.
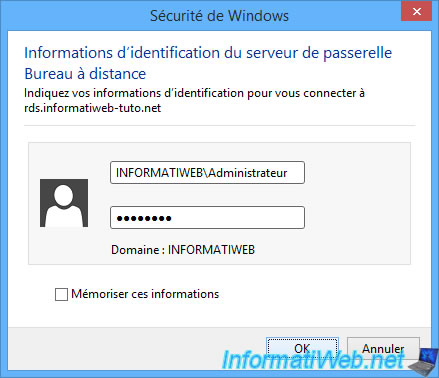
Then, Windows will try to connect to the desired local resource.
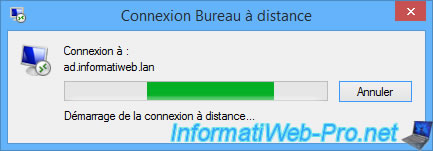
But, to access it, you will have to re-enter identifiers allowing you to connect to it.
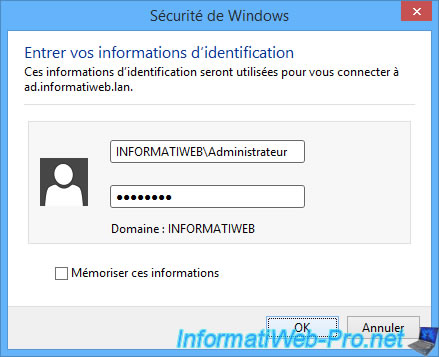
Finally, Windows will configure the remote connection.
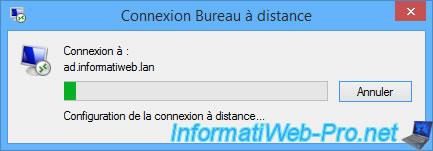
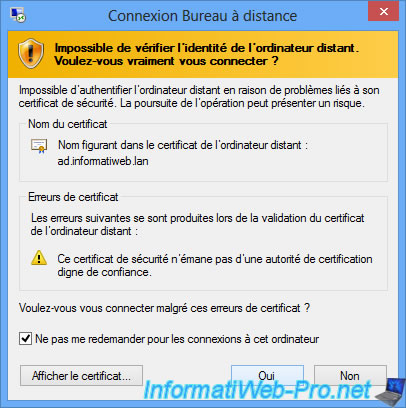
Ignore the "The identity of the remote computer cannot be verified" warning that appears.
This is because Windows Server uses self-signed certificates for the remote desktop by default.
If you want to remove these warnings, check the "Don't ask me again for connections to this computer" box or add valid (not self-signed) SSL certificates to your local servers.
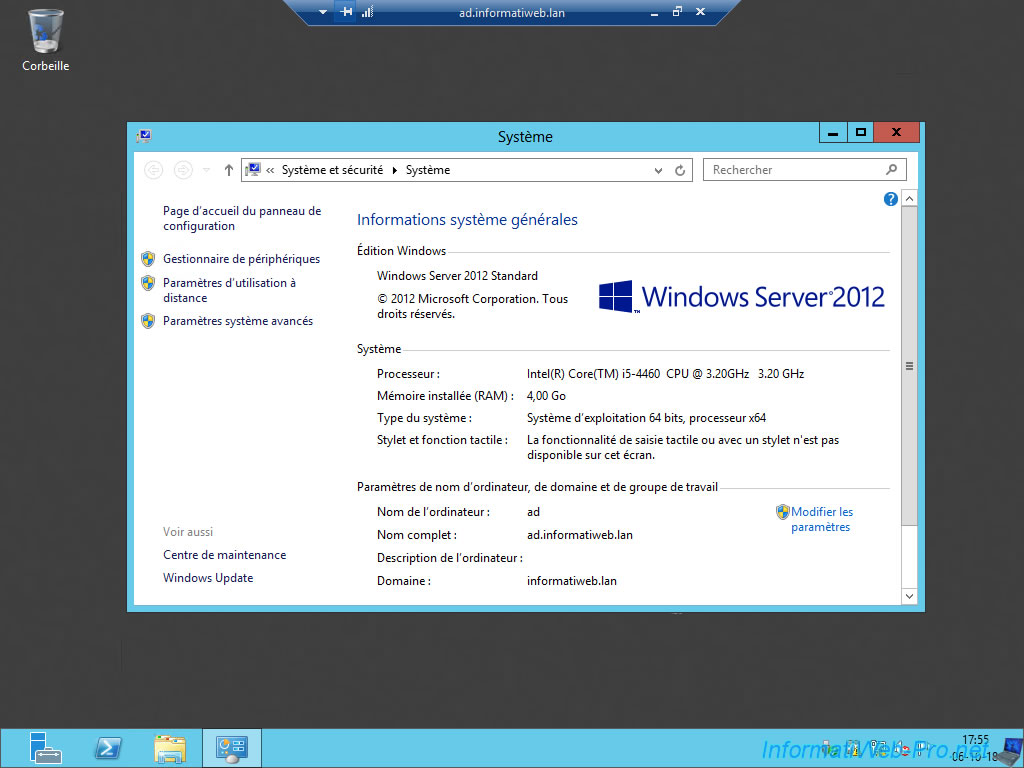
If all goes well, you can access your remote Active Directory server.
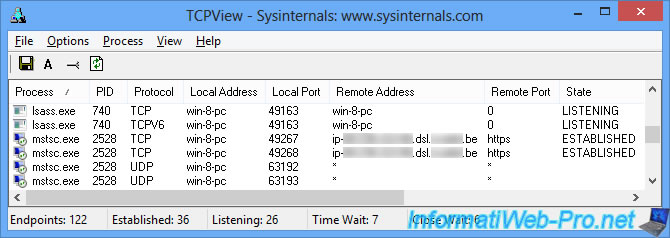
If you download and run the TCPView program of Sysinternals (Microsoft), you will see that the RDP client actually connects to your company's external IP address on the https (443) port.
Share this tutorial
To see also
-

Windows Server 6/7/2019
WS 2012 / 2012 R2 - RDS - Set up HA on your RDS infrastructure
-

Windows Server 3/8/2019
WS 2012 / 2012 R2 / 2016 - RDS - Access RemoteApp via a modern application
-

Windows Server 4/28/2019
WS 2012 / 2012 R2 / 2016 - RDS - Attempt to unblock the session as a user
-

Windows Server 3/16/2019
WS 2012 / 2012 R2 / 2016 - RDS - Change the properties of RemoteApps

No comment