Manage Group Policies (GPO) in an Active Directory infrastructure on Windows Server 2016
- Windows Server
- 16 July 2021 at 07:57 UTC
-

- 2/2
6. Applying Group Policies and GPO properties
For this tutorial, we will apply group policies to disable automatic updates on client PCs.
Indeed, in business, it often happens that the installation of Windows updates and other software is managed through third-party solutions, such as Microsoft SCCM (System Center Configuration Manager).
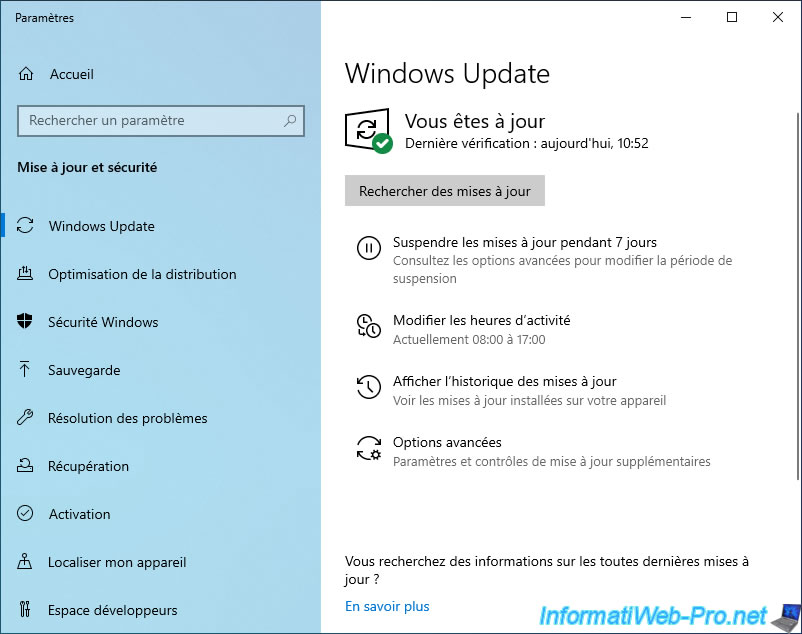
To disable updates on client PCs, go to : Computer Configuration -> Policies -> Administrative Templates ... -> System -> Internet Communication Management -> Internet Communication settings.
In this folder, double-click on the "Turn off access to all Windows Update features" policy.
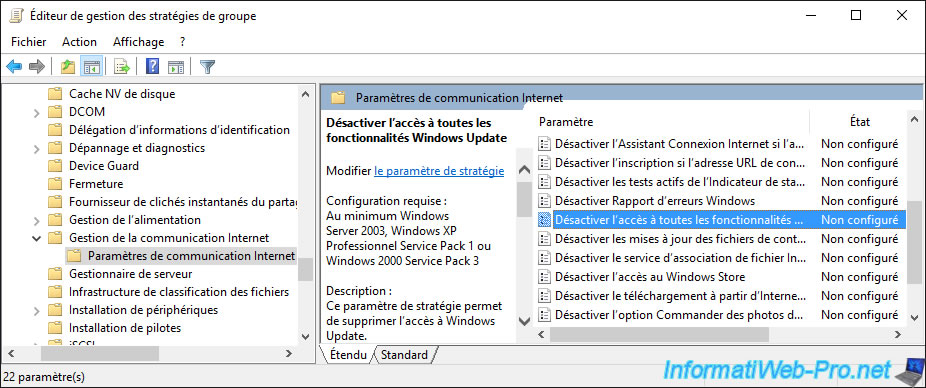
Enable this policy setting to remove Windows Update feature.
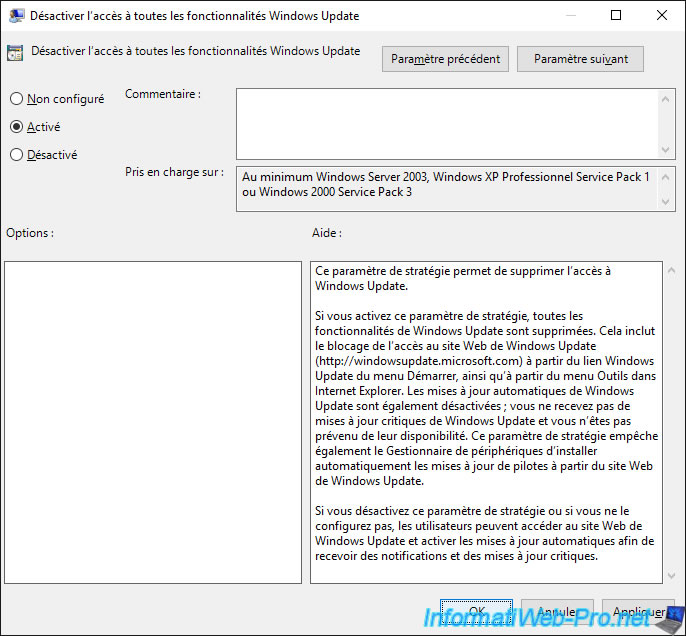
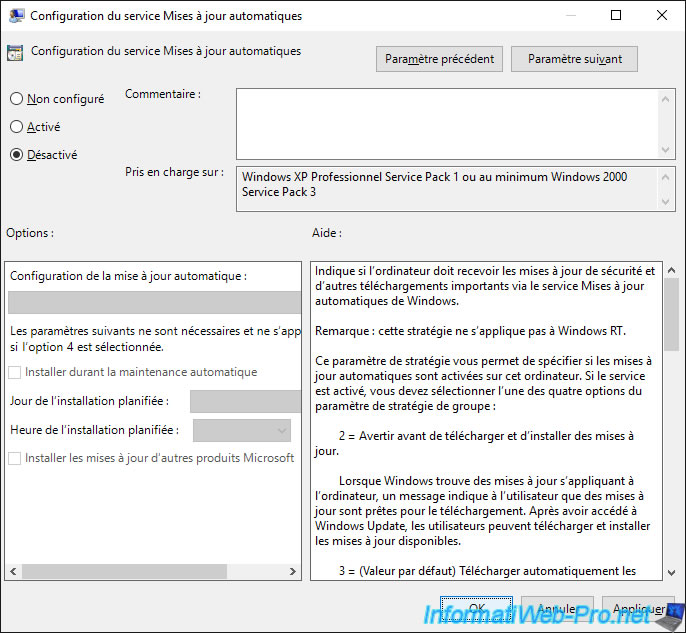
Then, go to "Computer Configuration -> Administrative Templates ... -> Windows Components -> Windows Update" and double-click on the "Configure Automatic Updates" policy.
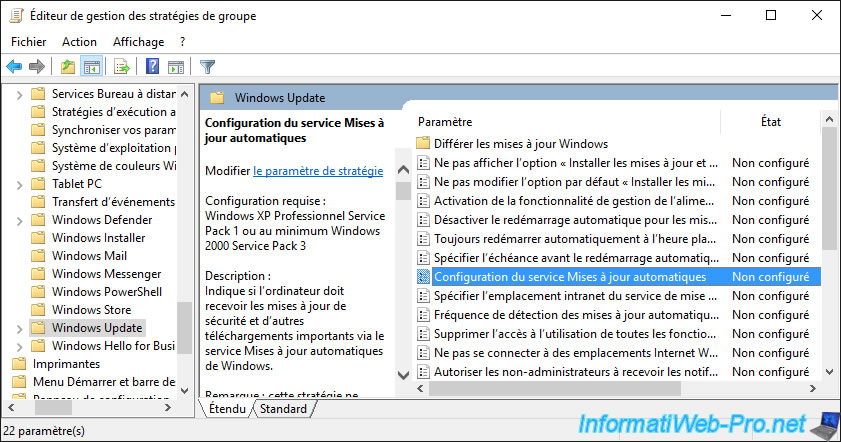
Disable this policy setting so that Windows Update is disabled on client PCs.
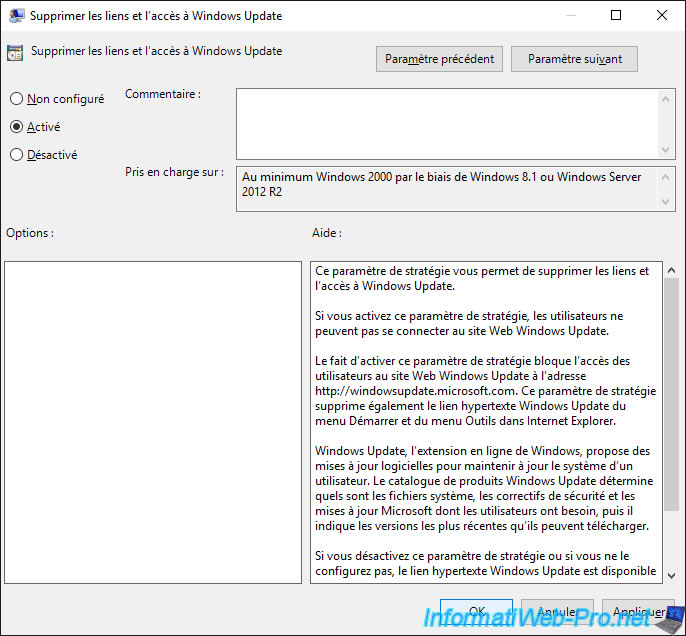
Finally, go to "User Configuration -> Policies -> Administrative Templates -> Start Menu and Taskbar" and double click on the "Remove links and access to Windows Update" policy.
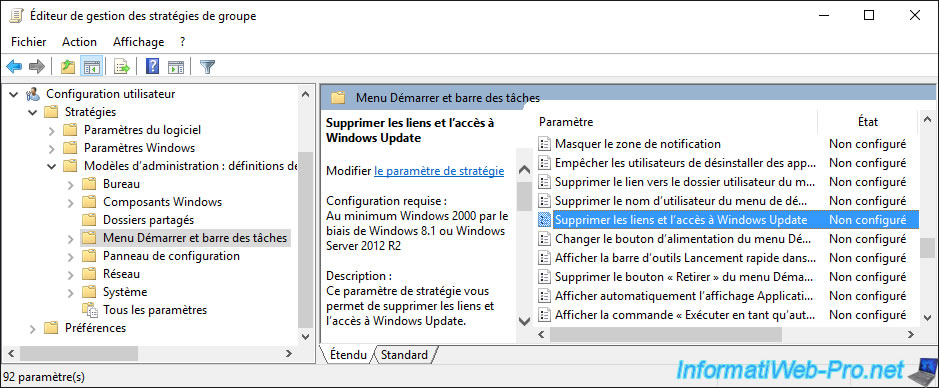
Enable this policy setting to block access to the Windows Update website.
As indicated in the description of this strategy.
Our GPO is created and configured, but it's not linked to any server or computer at this time.
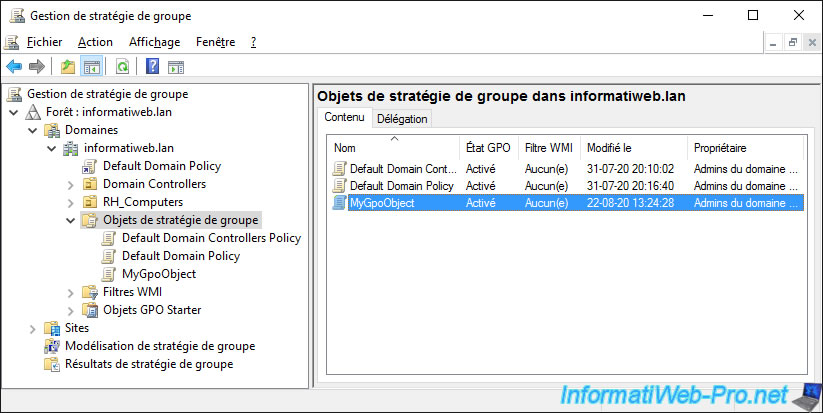
If you display the properties of this GPO by double-clicking on it, you will see that it's part of the Active Directory domain specified above, but that it's not linked to any site or domain Active Directory nor to an organizational unit.
Therefore, this Group Policy Object (GPO) is not used at this time.
By default, security filtering is "Authenticated Users" and WMI filtering is not used.
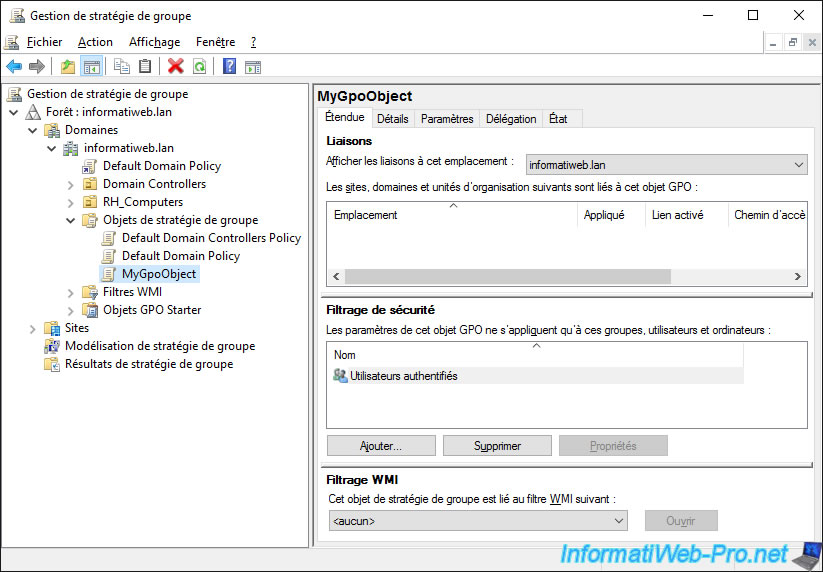
In the "Details" tab of the GPO object, you can find out :
- the Active Directory domain (or subdomain) in which it's located
- his owner
- his date of creation and last modification
- its user and computer version. This is used for data replication between multiple domain controllers present in the same domain (if applicable)
- its unique ID which corresponds to the name of the folder of this GPO present in : C:\Windows\SYSVOL\domain\Policies
- the Group Policy status (GPO)
- a comment (if there is one)
For the GPO state, by default, the "Computer configuration" and "User configuration" sections are both enabled, but you can also choose :
- to enable only the "Computer Configuration" section by selecting : User configuration settings disabled
- to enable only the "User Configuration" section by selecting : Computer configuration settings disabled
- to disable the 2 configuration sections to try to find the cause of a problem on a server or a client PC, for example, by selecting : All settings disabled
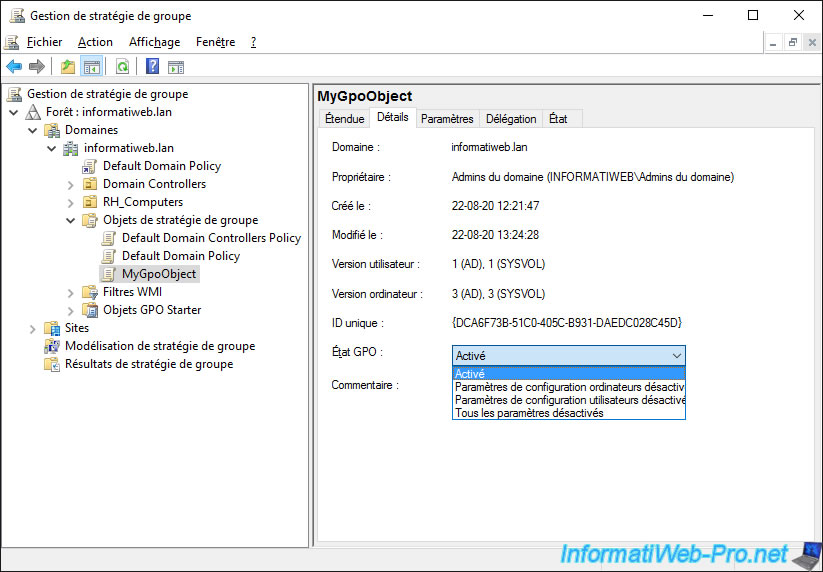
In the "Settings" tab of the GPO, you will be able to see which policies are defined in it, as well as their value.
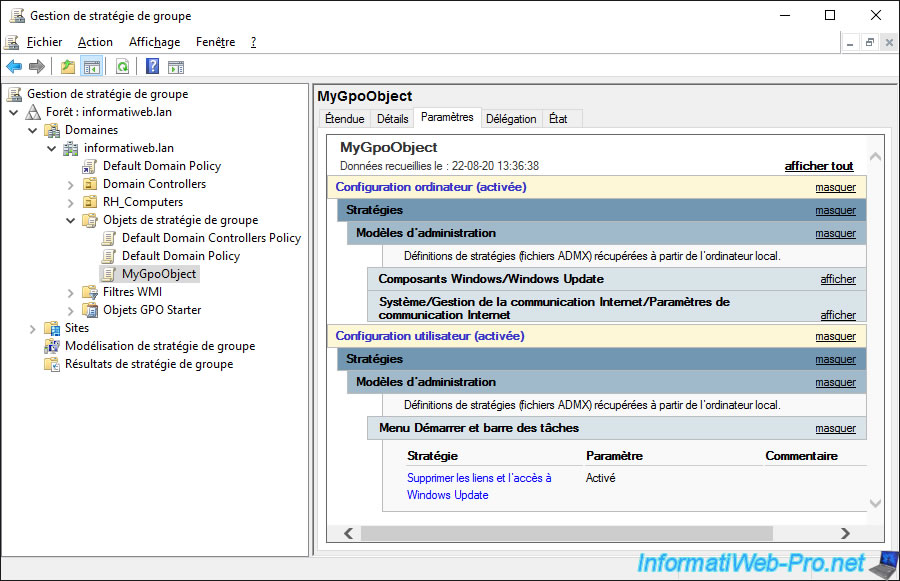
In the "Delegation" tab of the GPO object, you can delegate the management of this GPO object if you wish.
As you can see, by default :
- only administrators can edit the GPO object
- authenticated users only have read permission so that group policies can be read and applied on the client computer.
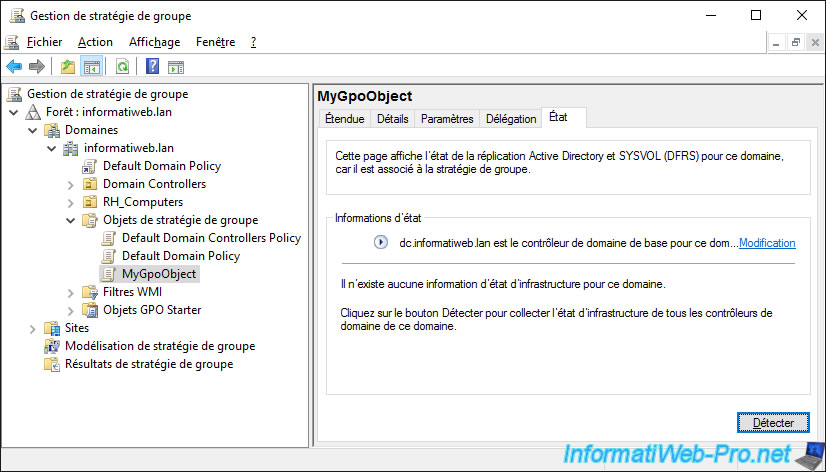
In the "Status" tab of the GPO object, you can find out the status of its replication on your different domain controllers if you have more than one domain controller.
7. Link a GPO object
Now that the GPO is created and configured, you can link it anywhere you want by right-clicking "Link an Existing GPO" on the desired item (in our case : the "RH_Computers" organizational unit).
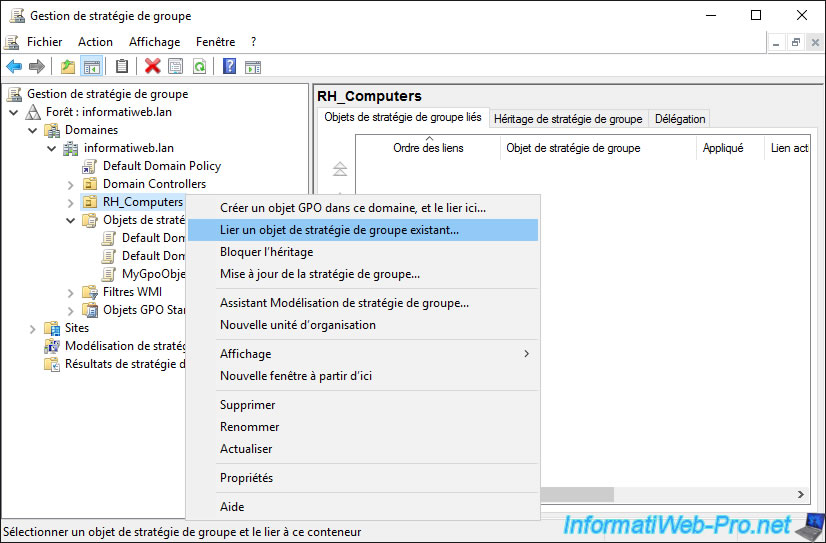
Select the GPO object created previously.
By selecting the OU to which you linked your GPO, you will see that your Group Policy Object (GPO) is linked to it.
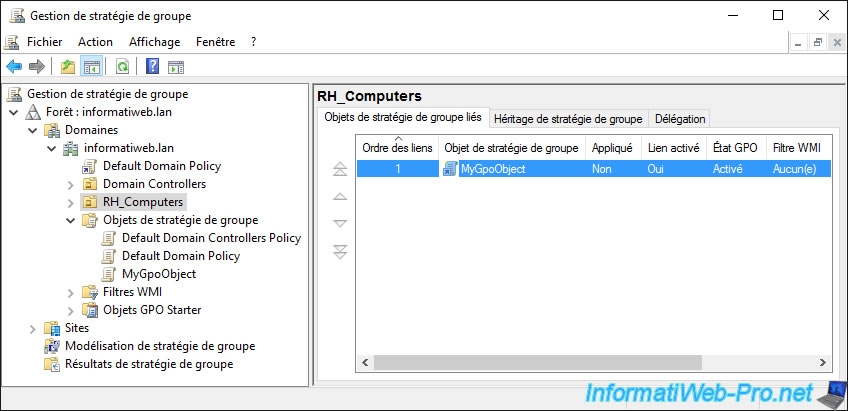
If you select the GPO, you will see in the "Scope" tab that it's indeed linked to a location : your "RH_Computers" organizational unit.
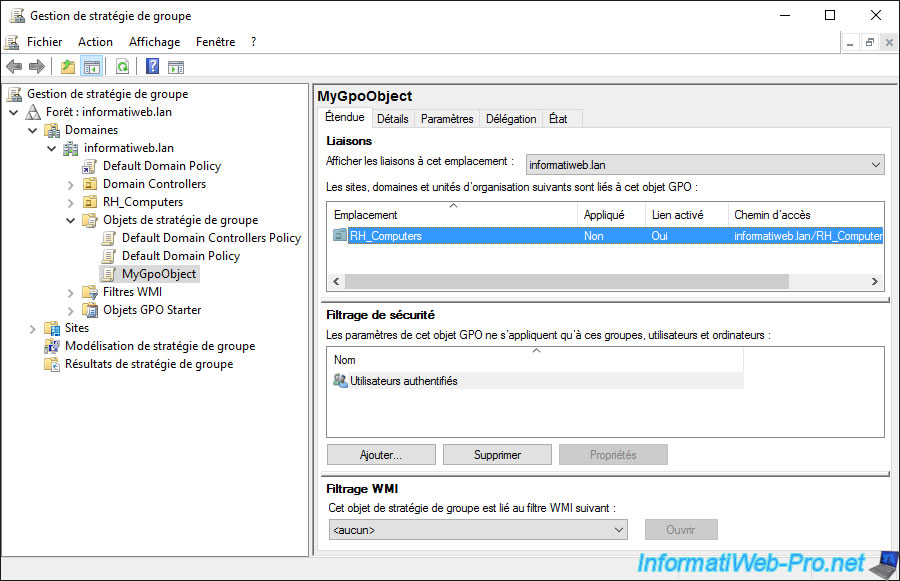
8. Update client PC Group Policies
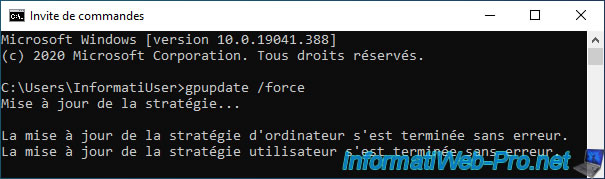
On the client PC, force the policy update by launching a command prompt as administrator, then typing the command :
Batch
gpupdate /force
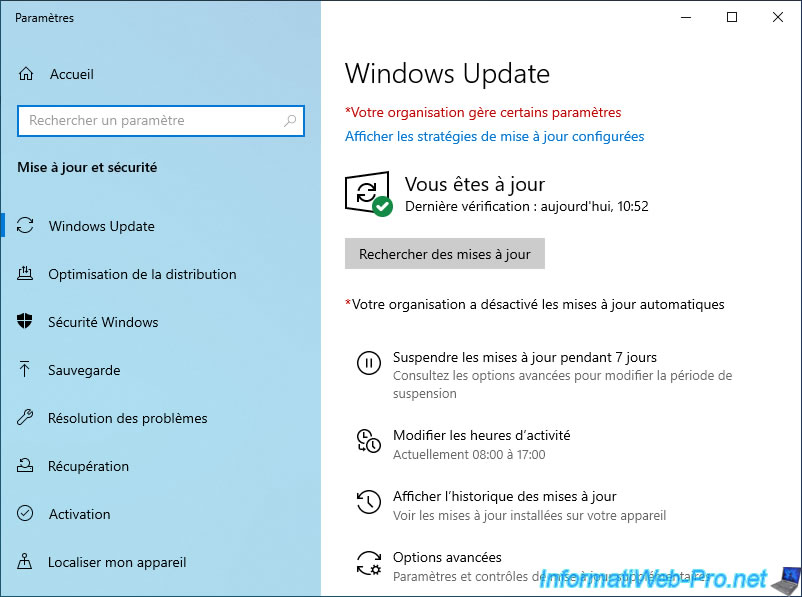
If you open Windows Update settings, you will see the "*Some settings are managed by your organization" message will be displayed in red.
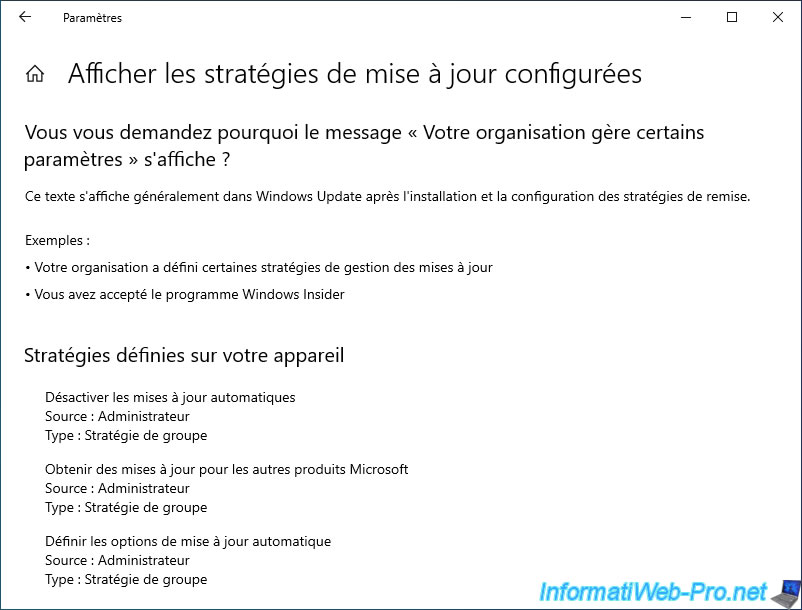
If you click on the "View configured update policies" link just below the message, you will be able to see which policies have been applied for Windows Update.
9. Display the policies applied on the client PC (RSOP)
On Windows 10, you will find a program named "rsop.msc" which allows you to easily know which group policies have been applied on this client PC.
There are other official alternatives to this program, but in this case, we will use this one.
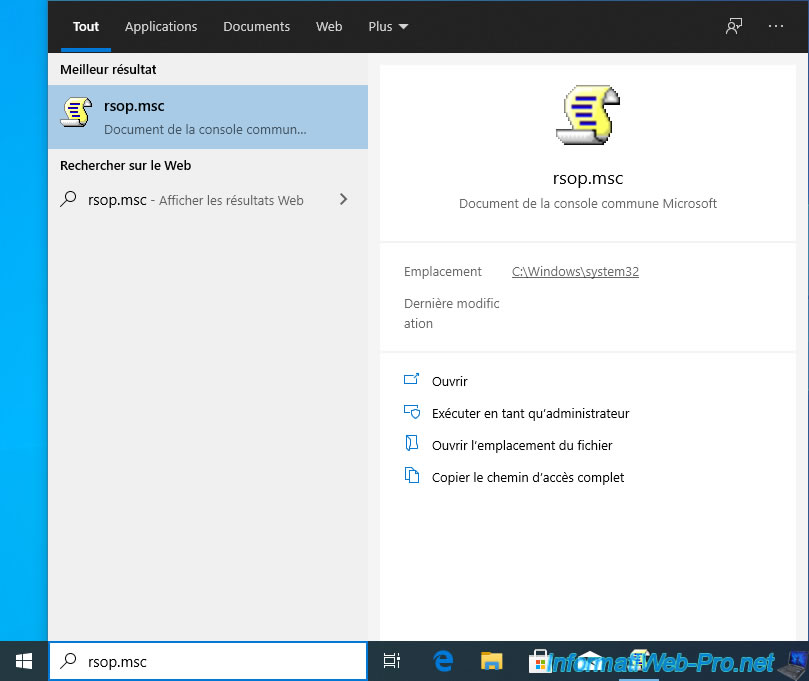
A "The resulting strategy set is being processed" window will be displayed.
While the policies data are loading, you will be able to see which user and which computer is used to obtain group policies.
This can help you find the cause of the application or not of a specific GPO.
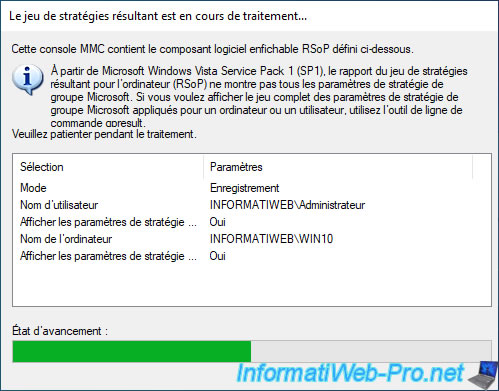
In our case, we find, for example, the group policy "Configure Automatic Updates" located in the "Computer Configuration" section.
Additionally, "rsop.msc" tells us what value has been assigned for this policy and what GPO it's from.
Share this tutorial
To see also
-

Windows Server 4/16/2021
Windows Server - AD DS - How Active Directory replication works
-

Windows Server 4/30/2021
Windows Server - AD DS - Overview of Active Directory functional levels
-
Windows Server 4/3/2021
Windows Server - AD DS - The basics of Active Directory
-

Windows Server 5/21/2021
WS 2016 - AD DS - Add a domain controller to an existing AD domain

No comment