Monitor or control the sessions of your users (Session Shadow) on Windows Server 2012 R2 / 2016
- Windows Server
- 03 May 2019 at 18:34 UTC
-

- 2/2
4. Permission required by default
Note that the user authorization request is, by default, required.
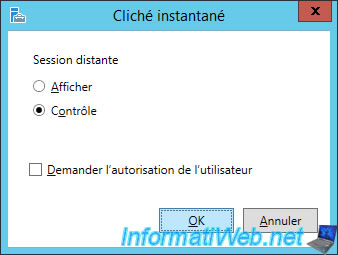
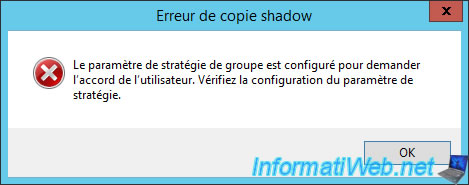
If you uncheck the box "Prompt for user consent", you will automatically receive an error message :
Plain Text
The Group Policy setting is configured to request the user's consent. Verify the configuration of the policy setting.
5. Make optional the user consent prompt
As previously explained, by default, you request the user's consent to see what he is doing and to control his session.
This practice is recommended in companies, because your users may be working on important projects and/or confidential documents (which you should not see).
This means that you should not disable this user consent prompt, which is mandatory by default.
Nevertheless, if you want to make it optional, here's how.
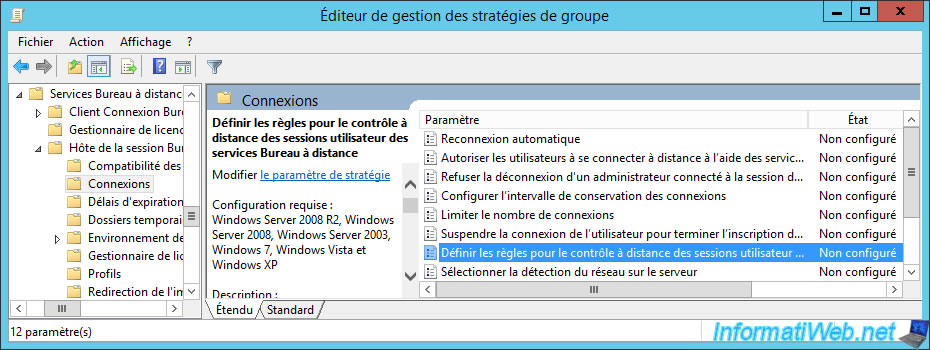
On your Active Directory server, open Group Policy Management and go to : Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Connections.
Then, double-click on the "Set rules for remote control of Remote Desktop Services user sessions" policy.
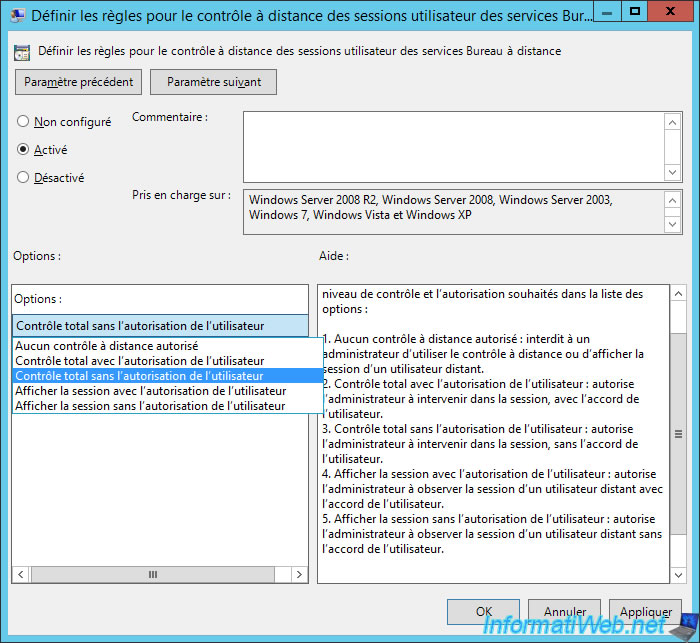
Enable this policy, then choose the desired option :
- No remote control allowed
- Full Control with user's permission
- Full Control without user's permission
- View Session with user's permission
- View Session without user's permission
In this tutorial, we will allow the administrator to control a remote user session without asking permission from the user.
Force the Group Policy update on your Session Host server, and then open the Server Manager again.
Then, go to : Remote Desktop Services -> Collections -> Name of the desired collection -> Right click on a user logged in to this session -> Shadow.
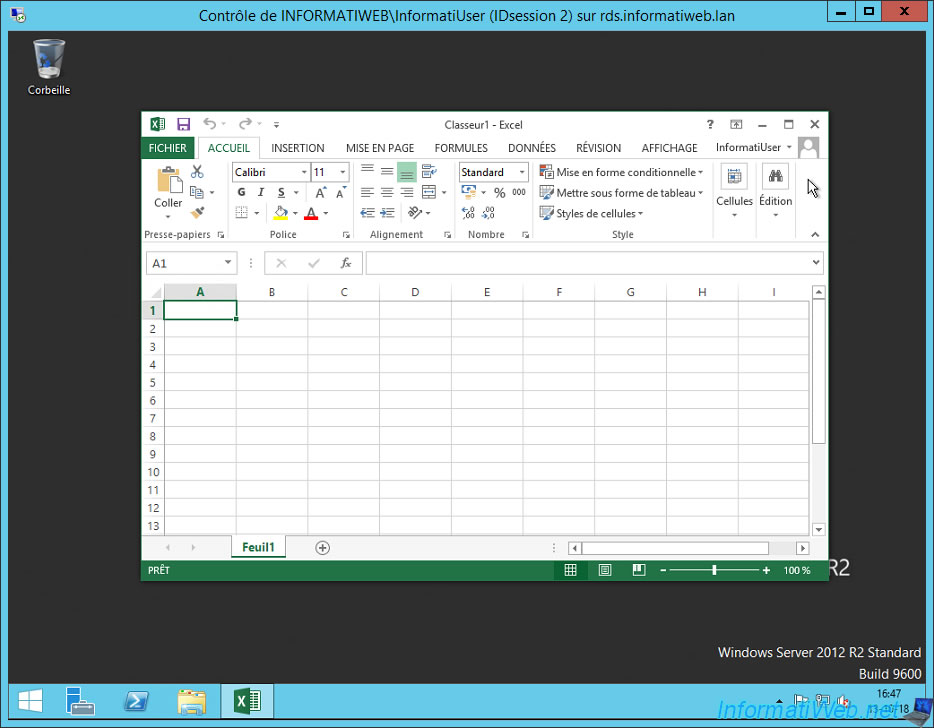
Now, we select "Control" and uncheck the "Prompt for user consent" box.
As expected, we can remotely control the session of our user without being notified and without his agreement.
Note that if you disable this consent request, you should first notify your users that their sessions can be monitored and/or controlled remotely without prior request.
6. View or control a user's session from the command line (CLI)
For those who wish to do the same thing via the command line, here's how to do it through the mstsc.exe process.
To view or control a session remotely from a command prompt, you will first need to know the session ID of the user.
To do this, open a command prompt as an administrator and use this command :
Batch
query session
In our case, this command shows us this :
Plain Text
SESSIONNAME USERNAME ID STATE TYPE DEVICE services 0 Disc >console Administrator 1 Active rdp-tcp#3 InformatiUser 2 Active rdp-tcp 65536 Listen
Now, we know that our InformatiUser user has the session ID : 2.
To know the parameters that you can use with the mstsc.exe program, use the command :
Batch
mstsc /?
6.1. View a user's session from the command line
To view a user's session, use this command by replacing the number 2 with the session ID of the desired user :
Batch
mstsc /shadow:2
Your user will be notified that you are trying to monitor their session remotely and will be able to accept or reject your request.
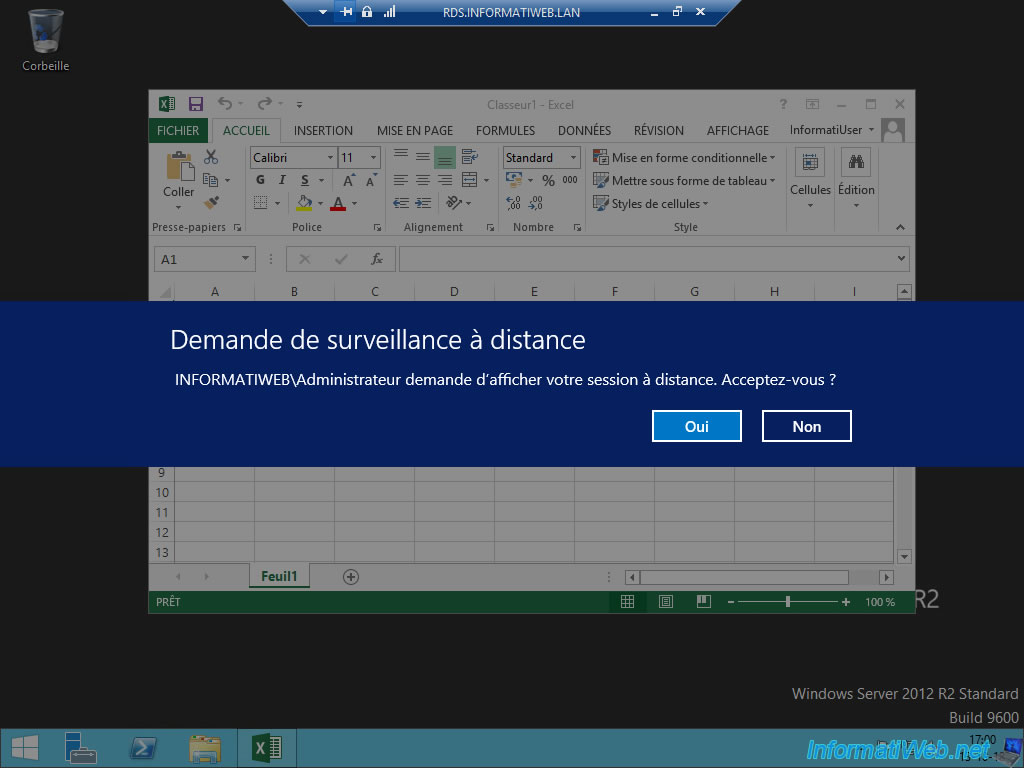
A remote desktop connection is made.
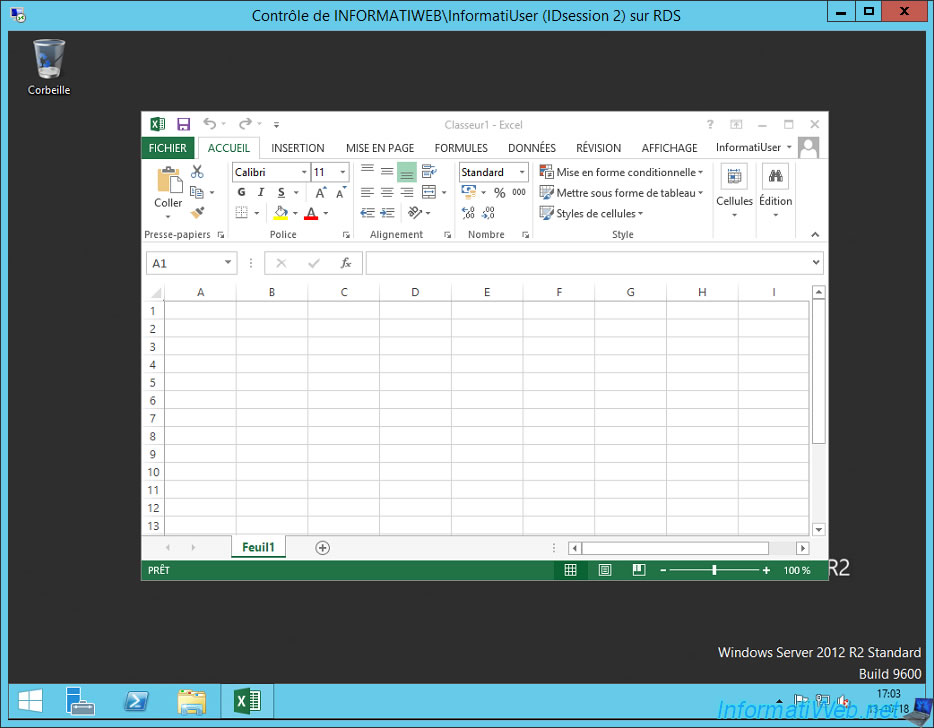
As you can see in the title of the window, it's a display of your user's session whose ID is in our case : 2.
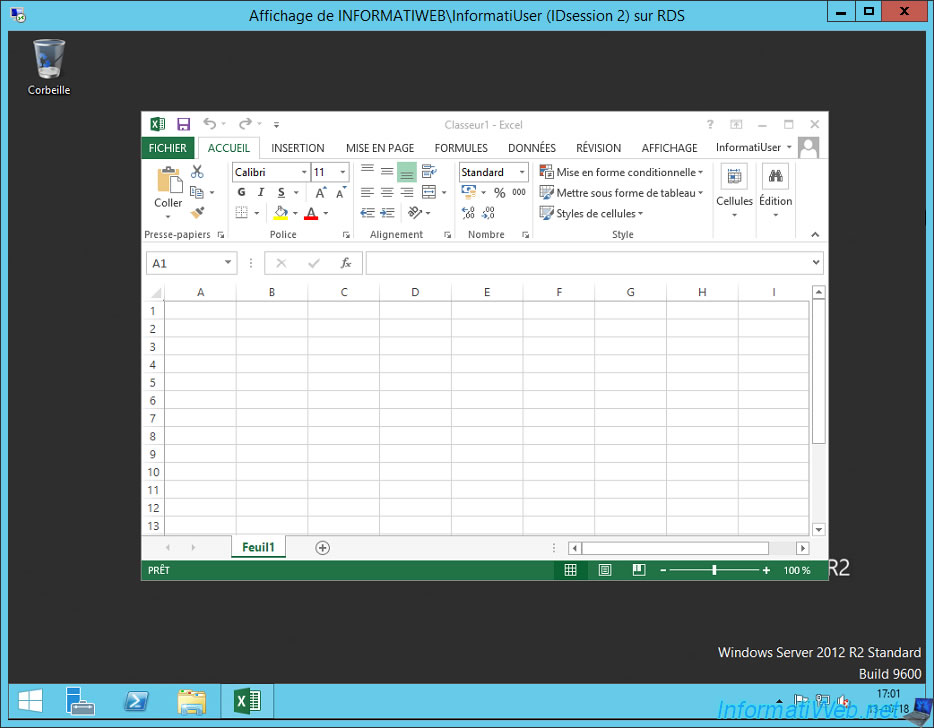
6.2. Control a user's session from the command line
To control a user's session, the command is almost identical.
Indeed, you just need to add this parameter : /control
Batch
mstsc /shadow:2 /control
In this case, your user will be notified that you want to control their session remotely.
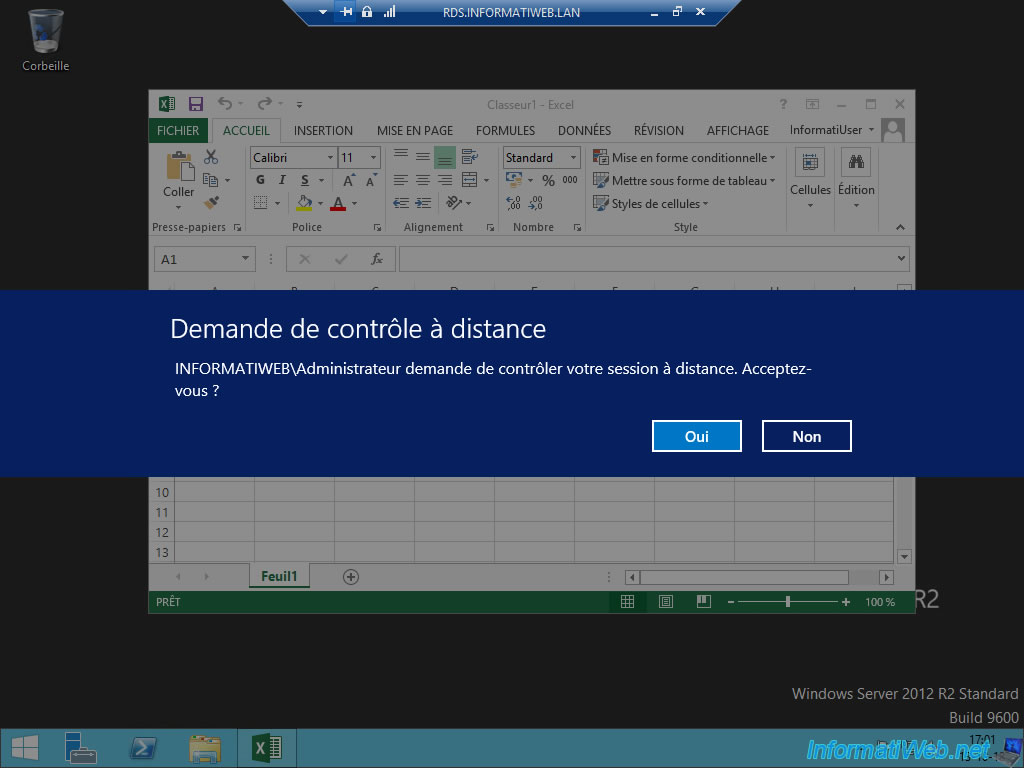
The "Remote Desktop Connection" window of the RDP client appears.
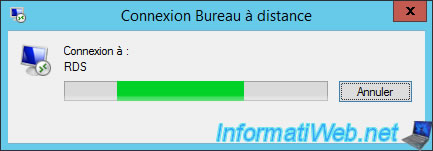
This time, the "Control" word appears in the title of the window, so you can control the remote user's session.
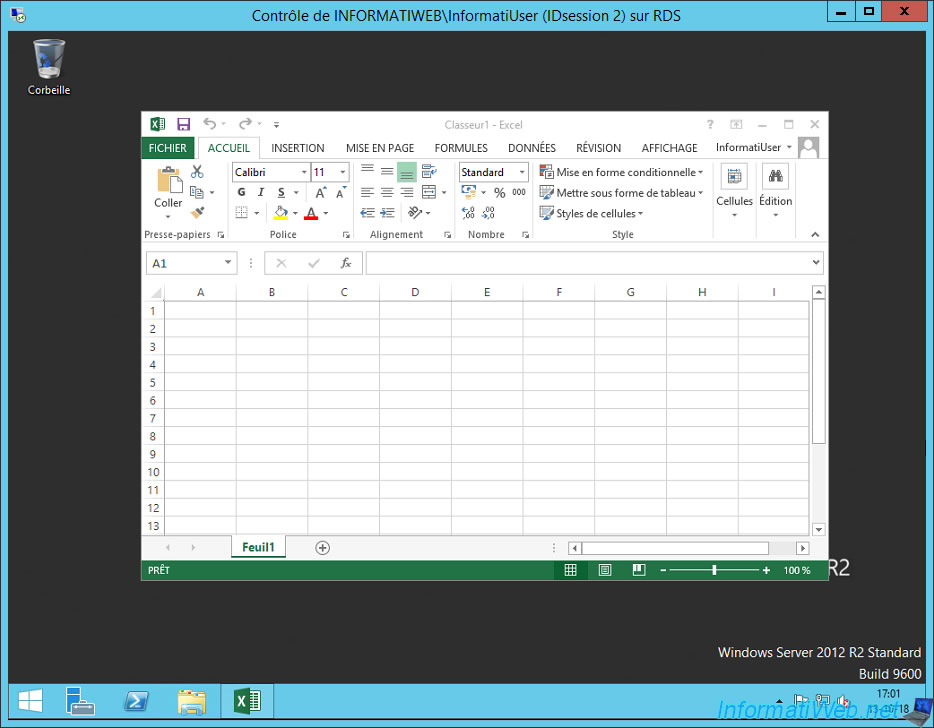
6.3. Control a user's session from the command line (without asking user consent)
As with the GUI, you can also view or control a remote session without asking for user consent.
Nevertheless, the strategy of your server must allow you to do it and this isn't the case by default (as explained above).
Once you have changed and updated the session host server policy as explained in step "5. Make optional the user consent prompt" of this tutorial, you will be able to control your user's session like this :
Batch
mstsc /shadow:2 /control /noConsentPrompt
Once the command is executed, you will have remote access to your user's session.
Share this tutorial
To see also
-

Windows Server 6/7/2019
WS 2012 / 2012 R2 - RDS - Set up HA on your RDS infrastructure
-

Windows Server 3/8/2019
WS 2012 / 2012 R2 / 2016 - RDS - Access RemoteApp via a modern application
-

Windows Server 4/28/2019
WS 2012 / 2012 R2 / 2016 - RDS - Attempt to unblock the session as a user
-

Windows Server 3/16/2019
WS 2012 / 2012 R2 / 2016 - RDS - Change the properties of RemoteApps

No comment