- Windows Server
- 30 March 2019 at 10:27 UTC
-

When creating a RDS infrastructure, it's important to secure communications between client PCs and your session hosts servers to prevent interception and/or modification of the data passes through your local network.
Indeed, since your users are working on remote desktop and/or RemoteApp programs, everything they do could be seen in the network if it was not encrypted (secure).
However, you should also know that there are different levels of encryption that are more or less secure and are sometimes compatible with some versions of Windows (or any other operating system).
- Set the level of encryption to use through group policies (GPO)
- Set the level of encryption to use through the server manager
- Set the encryption level to use via the registry (not recommended)
1. Set the level of encryption to use through group policies (GPO)
To set the level of encryption to use in your RDS infrastructure using Group Policies, you will need to go to your Active Directory server.
In the Group Policy Management Editor, go to : Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Security.
Then, double-click on the "Set client connection encryption level" policy.
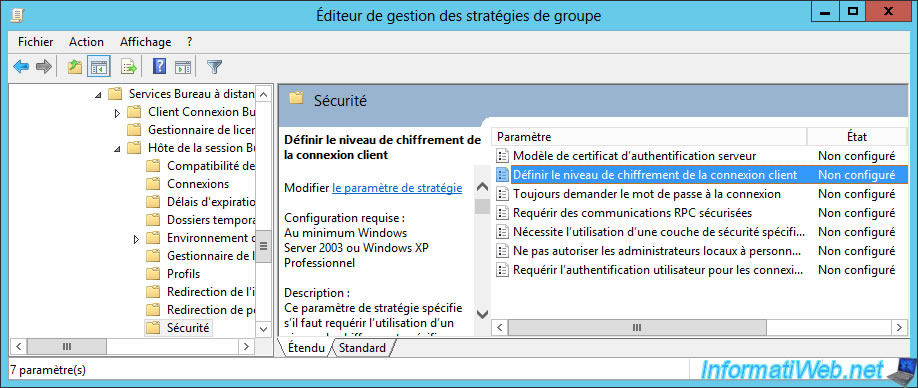
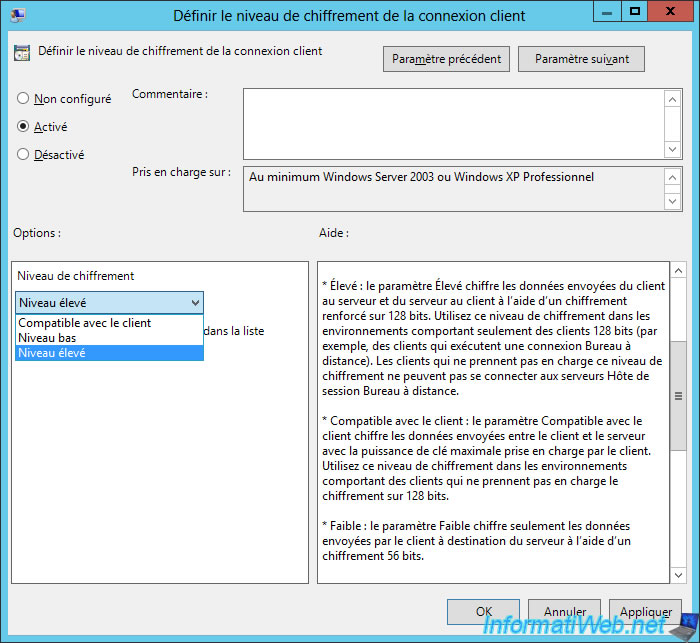
Enable this policy and choose the desired encryption level :
- Client Compatible : use the highest level of encryption that is compatible with the server and the client. But, this can pose a security problem if you log in from an old client machine or through an older version of an RDP client.
- Low Level (or Low) : encrypts data sent by the client to the server with a 56-bit key. But this doesn't encrypt the data in the other direction (from server to client).
- High : allows you to encrypt data sent in both directions.
Warning : if you use the high level of encryption (which allows you to better secure the connection between the server and the client), the 128-bit encryption must be supported by the RDP client of your user to connect to your server.
Otherwise, the RDP connection will be refused, even if the credentials were good.
Although you probably will not need it, be aware that there is an even better level of encryption based on the use of certificates (PKI) called FIPS.
To use it, you will need a PKI infrastructure and you will have to activate FIPS support via group policies.
To do this, go to "Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options".
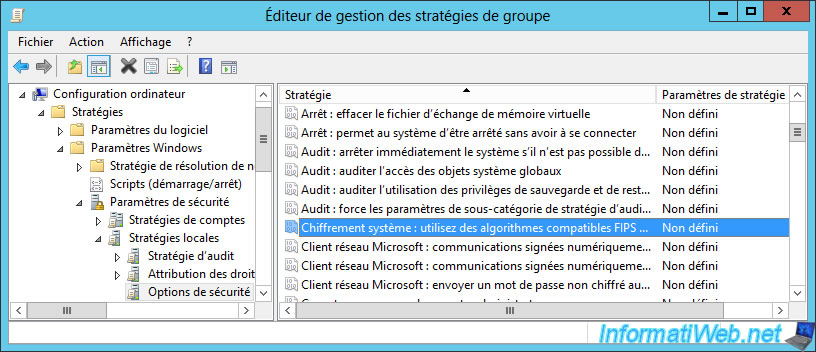
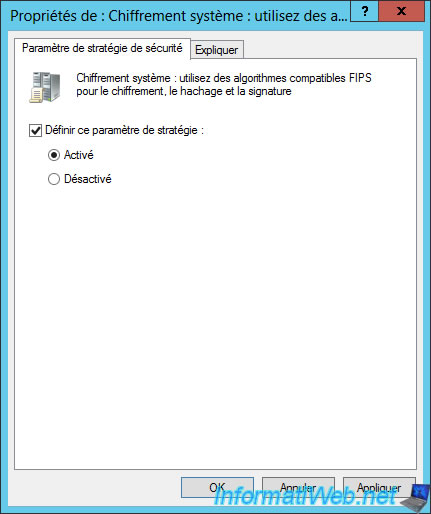
Then, enable the "System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing" policy.
2. Set the level of encryption to use through the server manager
If you don't want to set the encryption level through group policies, you can also do this through the server manager.
Nevertheless, you will have to do it for each collection. This can quickly become unmanageable if you have a lot of collections in your RDS infrastructure.
To begin, go to the properties of each collection.
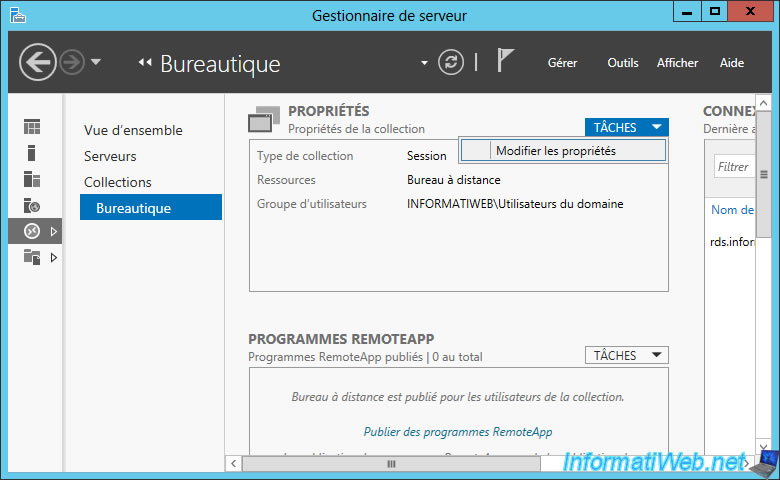
Then, select the encryption level to use.
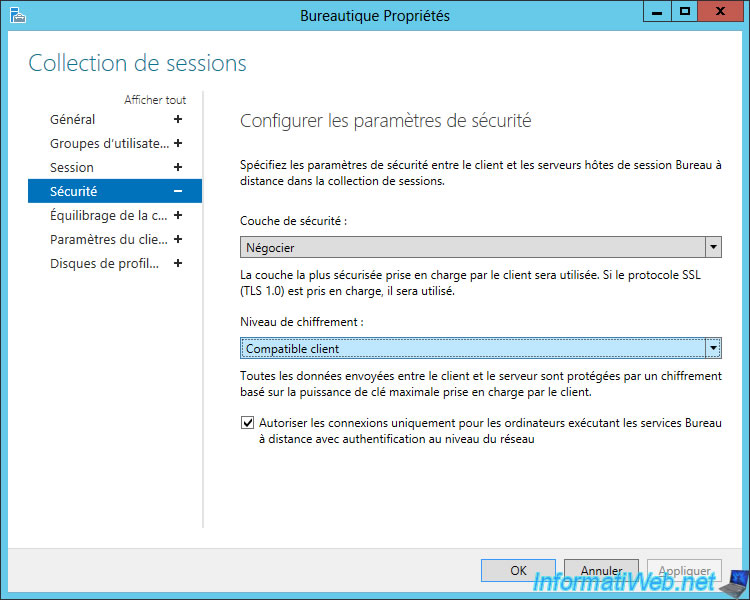
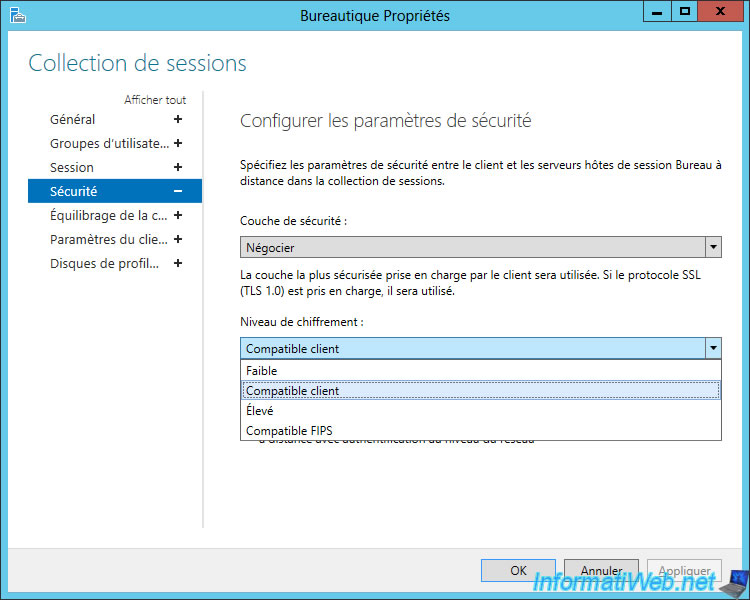
As you can see, there are 4 encryption levels :
- Low (or low level)
- Client compatible (negotiate)
- High (or high level)
- FIPS compatible (requires PKI and certificate management)
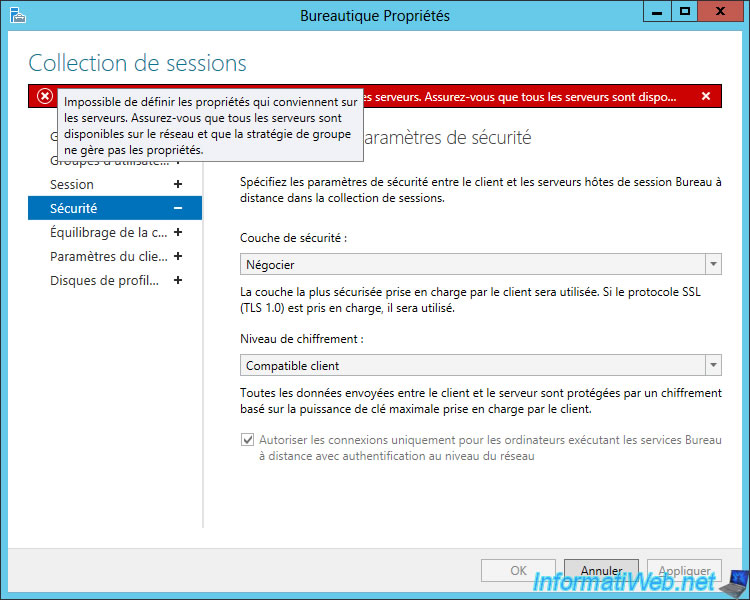
Note that, as for the selection of the security layer, the parameter selected via group policies (if applicable) will have priority over the choice available in the properties of each collection.
3. Set the encryption level to use via the registry (not recommended)
Although this is NOT recommended and that this requires a restart of the RD Session Host server (which is rather complicated in a production environment), know that it's still possible to do it via the registry.
To do this, run the "regedit.exe" program on the desired session host server and navigate to this key : HKLM\SYSTEM\CurrentControlSet\Control\TerminalServer\WinStations\RDP-Tcp
In this "RDP-Tcp" key, you will find a data named "MinEncryptionLevel".
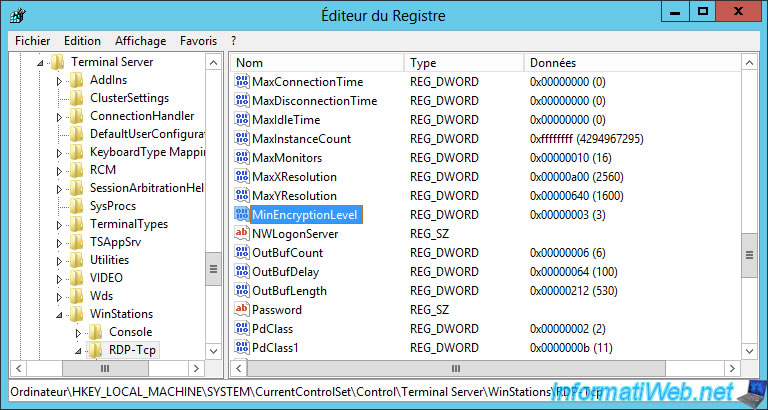
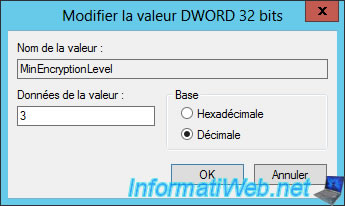
If you right-click "Edit" on it and select the "Decimal" base, you can choose the encryption level according to a number :
- 1 = Low or low level
- 2 = client compatible
- 3 = High level
- 4 = FIPS compatible
Source : WS2008: Network Level Authentication and Encryption (Microsoft)
After you change this value, close the registry editor and restart your session host server.
Share this tutorial
To see also
-

Windows Server 6/7/2019
WS 2012 / 2012 R2 - RDS - Set up HA on your RDS infrastructure
-

Windows Server 3/8/2019
WS 2012 / 2012 R2 / 2016 - RDS - Access RemoteApp via a modern application
-

Windows Server 4/28/2019
WS 2012 / 2012 R2 / 2016 - RDS - Attempt to unblock the session as a user
-

Windows Server 3/16/2019
WS 2012 / 2012 R2 / 2016 - RDS - Change the properties of RemoteApps


You must be logged in to post a comment