Create a root certification authority (Root CA) on Debian / Ubuntu
- Linux
- 14 February 2015 at 18:46 UTC
-

- 2/2
5. Securing Apache with the SSL certificate
In the configuration of a website secured with SSL, you will specify the following lines :
Bash
SSLEngine on SSLCertificateFile /etc/ssl/certs/www-cert.pem SSLCertificateKeyFile /etc/ssl/private/www-key.pem
For more information about securing an Apache web server, read our tutorial "Securing the Apache web server".
6. Test the configuration
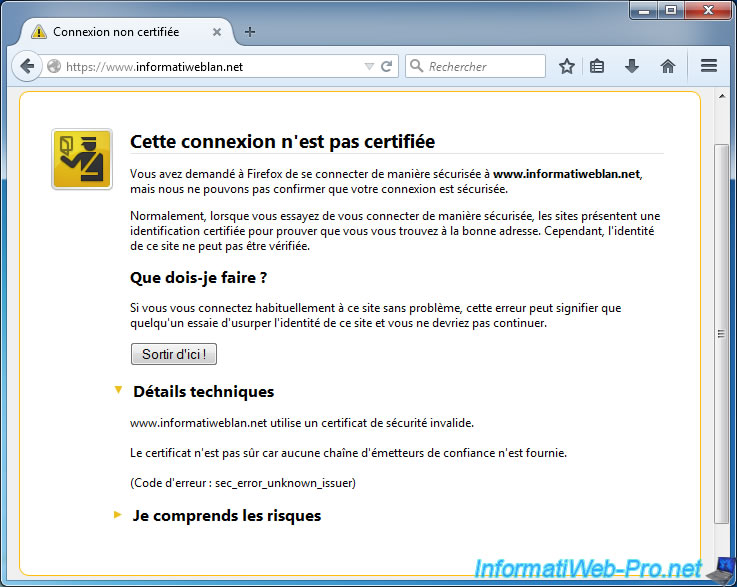
If you try to access the secure part of your website using the https protocol, you'll get a warning "This connection is not certified".
This is normal because our certification authority is not supported by default. To solve this problem, the user must add the certificate of your authority in his "trusted authorities" list of his computer (or smartphone, ...).
7. Import the certificate of the authority in Linux PC
For Linux PC, no problem. Just copy the certificate of the authority (only the certificate) in the web space of your server.
Bash
cp /usr/lib/ssl/misc/demoCA/cacert.pem /var/www/
Then, on client computers, go to the following address : http://www.informatiweblan.net/cacert.pem
Note : You must use the http protocol to download the certificate because the https version is blocked by the warning.
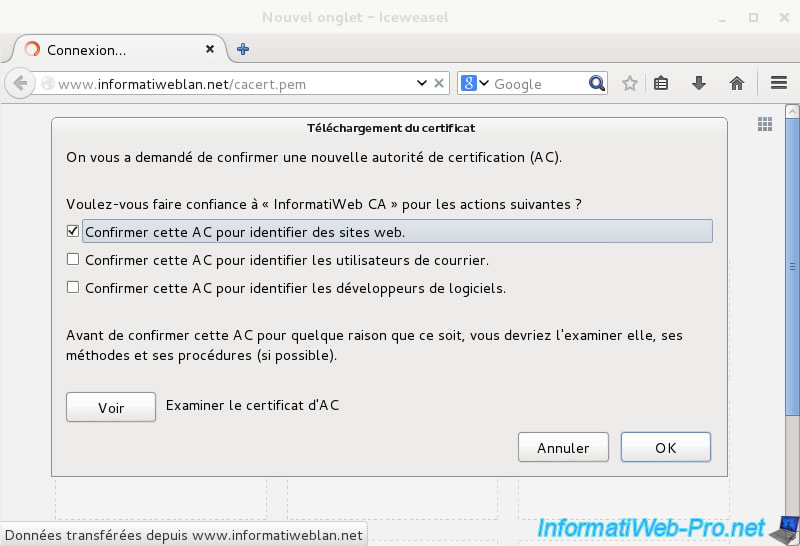
The web browser will ask you to confirm this new authority.
If using certificates only for your websites, check only the first box.
Otherwise, also check the other boxes as needed (for IMAP and POP3 protocol of your mail server, for example).
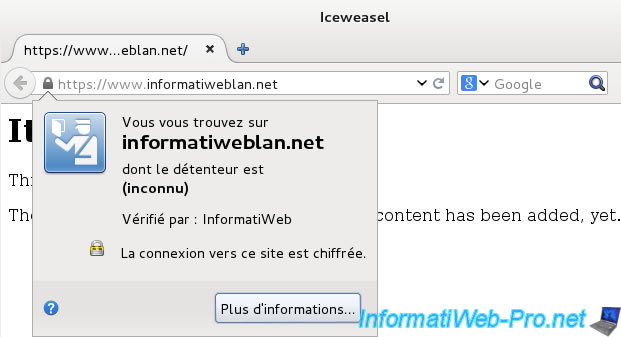
The web browser will no longer display a warning for certificates that you sign with your CA.
8. Import the certificate of the authority in Windows PCs
For Windows computers, you must convert the .pem certificate to .cer (Microsoft format).
To do this, make the conversion on the server by using "OpenSSL".
Bash
cd /usr/lib/ssl/misc/demoCA openssl x509 -inform PEM -in cacert.pem -outform DER -out cacert.cer
Then, copy this version of the certificate in the web space of your server.
Bash
cp /usr/lib/ssl/misc/demoCA/cacert.cer /var/www/
Then, on client computers, download the certificate of your certification authority at : http://www.informatiweblan.net/cacert.cer
Note : You must use the http protocol to download the certificate because the https version is blocked by the warning.
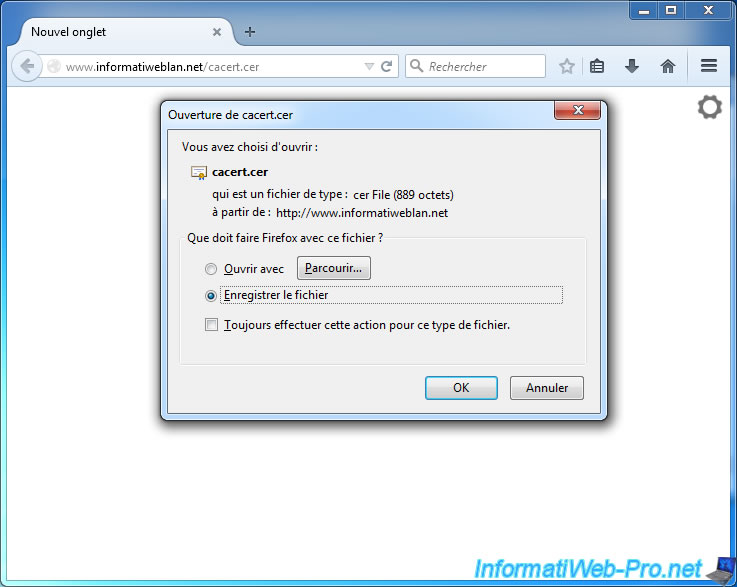
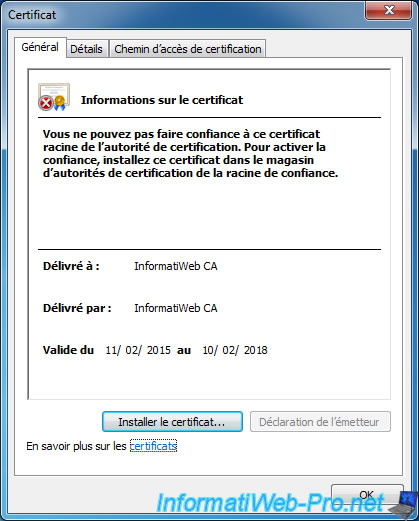
Open the certificate and click "Install Certificate".
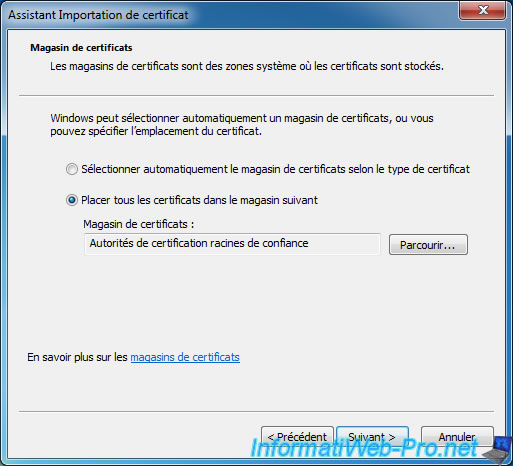
Click "Browse" and select the "Trusted Root Certification Authorities" store.
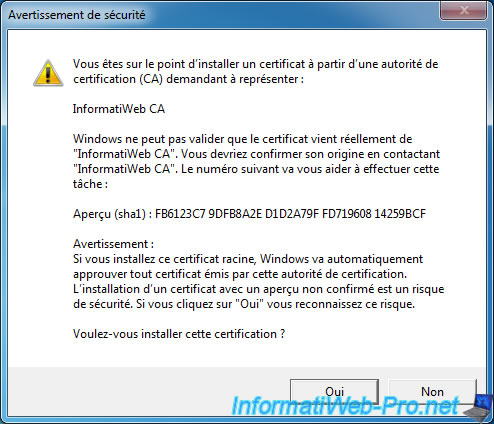
Confirm the certificate import of your CA by clicking "Yes".
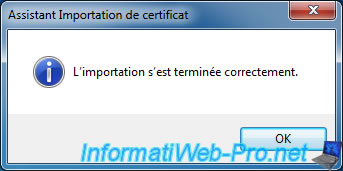
Web browsers "Internet Explorer" and "Google Chrome" use the Windows certificate store. So you will no longer have a warning for your certificates on these web browsers.
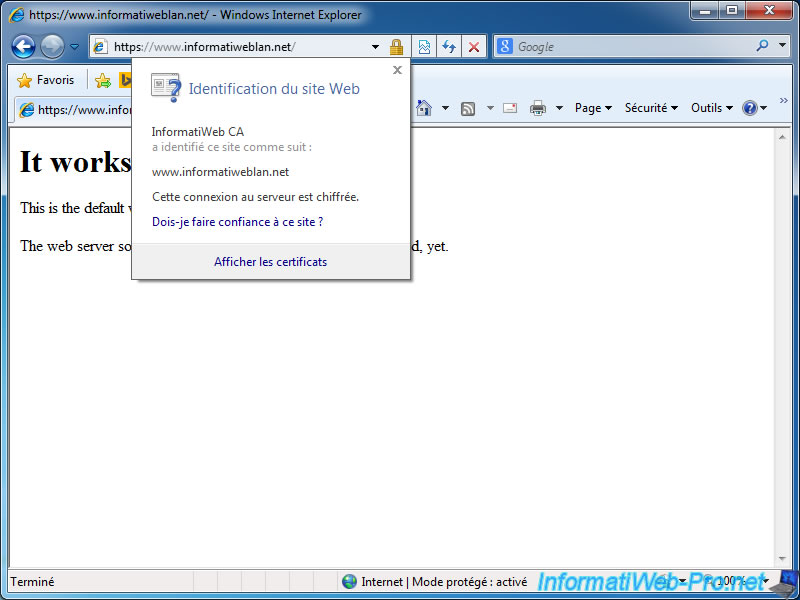
For Mozilla Firefox, open this browser and go to the menu (3 horizontal lines) -> Options -> Advanced -> Certificates -> View Certificates -> Authorities.
Then, click on the "Import" button and select the certificate of your authority.
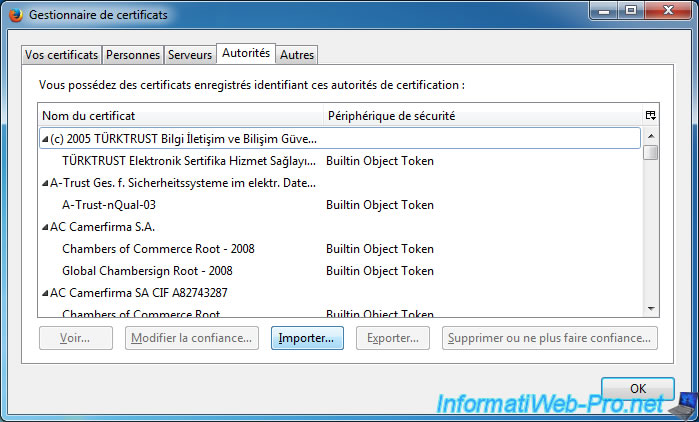
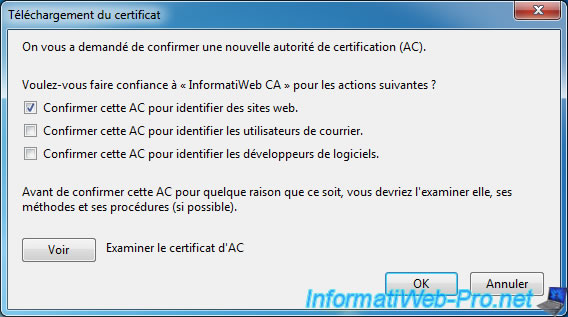
The web browser will ask you to confirm this new authority.
If using certificates only for your websites, check only the first box.
Otherwise, also check the other boxes as needed (for IMAP and POP3 protocols of your mail server, for example).
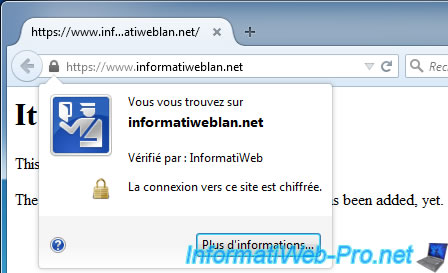
Now, Mozilla Firefox will no longer display warnings for certificates signed by your authority.
9. Revoke a certificate
To finish this tutorial on creating and using a Linux certification authority, here's how to revoke a certificate.
In other words : invalidate a certificate for one reason or another.
Bash
cd /usr/lib/ssl/misc openssl ca -revoke /etc/ssl/certs/www-cert.pem
Note : OpenSSL will ask you for the password of the private key of the authority to revoke the desired certificate.
Plain Text
Using configuration from /usr/lib/ssl/openssl.cnf Enter pass phrase for ./demoCA/private/cakey.pem: Revoking Certificate 9241C8A0FA4333F6. Data Base Updated
10. Create the revocation list (CRL)
Create the "crlnumber" file.
Bash
echo 1000 > /usr/lib/ssl/misc/demoCA/crlnumber
Then, create the revocation list (CRL)
Bash
cd /usr/lib/ssl/misc openssl ca -gencrl -out demoCA/crl/ca-crl.pem
According to the standard "RFC 5280", the revocation list must be encoded in DER :
Plain Text
Excerpt : If the DistributionPointName contains a general name of type URI, the following semantics MUST be assumed: the URI is a pointer to the current CRL for the associated reasons and will be issued by the associated cRLIssuer. When the HTTP or FTP URI scheme is used, the URI MUST point to a single DER encoded CRL as specified in [RFC2585].
To encode this list in DER format, use OpenSSL like this :
Bash
openssl crl -inform PEM -in demoCA/crl/ca-crl.pem -outform DER -out demoCA/crl/ca-crl.crl
11. Make the revocation list available from the web
To do this, copy the "ca-crl.crl" file in the web space of your server.
Bash
cp /usr/lib/ssl/misc/demoCA/crl/ca-crl.crl /var/www/ca-crl.crl
12. Test of the revocation
For this test to be correct, we will clear the cache of Windows revocation lists.
This will avoid you from having a revoked certificate that is not recognized as revoked.
To do this, type these two commands in a "Command Prompt" launched as administrator.
Clear the CRL (certificate revocation lists) cache of the HDD.
Batch
certutil -URLCache CRL –delete
Invalid the use of CRL cached in memory and the hard drive.
Batch
certutil –setreg chain\ChainCacheResyncFiletime @now
And finally, empty the cache of your browser. Thus, the revocation will be detected directly.
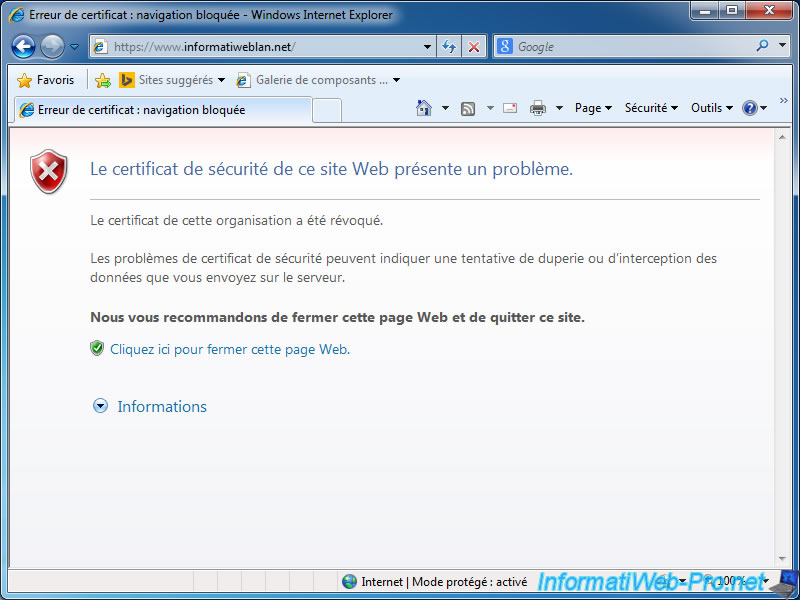
After 2-3 minutes, Internet Explorer and other browsers will block access to your website because the certificate has been revoked.
Here is the error in Internet Explorer.
Share this tutorial
To see also
-
Linux 10/5/2015
Network monitoring in real time with IPTraf
-
Linux 8/23/2016
PuTTY - Fix the issue with the numeric keypad
-

Linux 9/8/2016
StartSSL - Renew your SSL certificates
-
Linux 7/24/2015
StartSSL - Secure your website for free

Show comment